What if your security system could react the moment a device leaves the building—or a high-risk zone? That’s the power of geofencing in cyber security, and if your organization isn’t using it yet, you might already be behind.
Geofencing creates invisible, location-based boundaries that trigger automatic security actions—like locking a device, sending alerts, or restricting access—when crossed. And in a world where 70% of employees now work remotely at least once a week, protecting data outside the office walls has never been more critical.
With cyber threats evolving and sensitive data constantly on the move, businesses need smarter, faster ways to react. Geofencing helps IT teams move from passive monitoring to proactive security, ensuring that devices and data stay protected—no matter where they go.
In this guide, we’ll explore:
- What geofencing actually is
- How it works in the cybersecurity landscape
- Why it’s quickly becoming essential for modern device protection
- And how you can use it to level up your security posture
Don’t wait until a device goes missing across borders or connects to a rogue network. Let’s dive into how location-based security is transforming the way organizations protect their most valuable assets.
Understanding the power of geofencing in cybersecurity
Transitioning our focus to IT, geofencing provides impressive benefits to IT ops teams. It affords a paramount security layer that improves their capacity to monitor remote devices, protect the security system, safeguard confidential data, maintain compliance, and counteract with security action to prevent unauthorized access. Combining geofencing with multi factor authentication can provide an extra layer of security for sensitive systems, making unauthorized access even more difficult.
For example, IT teams can set up geofencing parameters to prevent access to sensitive data outside of specific locations, such as office premises, or a certain location defined by GPS or mapping tools, or secure remote networks. In this manner, whether an employee accidentally attempts to access their devices from an unsecured public network or a malicious attacker tries to breach through unfamiliar locations, the geofence will obstruct this activity and send immediate alerts to IT teams. Geofencing systems track a device's location in real time to determine if it is within an authorized area. Geofencing can also detect deviations from usual patterns of device movement, helping to identify potential security breaches.
What is a virtual boundary in geofencing?
Geofencing is a location-based technology that creates a virtual perimeter around a real-world geographic area. It uses GPS, RFID, Wi-Fi, or cellular data to trigger specific actions when a connected device enters or exits this defined zone. From retail to marketing, logistics, social networking services, healthcare and IT security, geofencing is used across a variety of sectors for different purposes.
Setting boundaries: how geofencing defines secure zones
Geofencing technology enables businesses to define secure zones by establishing virtual boundaries around specific geographical locations, such as offices, healthcare facilities, or other sensitive areas. These virtual boundaries are crucial for controlling access and protecting sensitive information. When a device enters or exits a geofenced area, geofencing technology can automatically trigger a range of security actions—such as sending real-time alerts to security teams, restricting network access, blocking access to certain data, or even encrypting sensitive information to prevent unauthorized use.
By setting virtual boundaries, companies can enhance security and prevent data breaches by ensuring that only authorized personnel can access sensitive data within designated areas. For instance, a healthcare facility might use geofencing to restrict access to patient records, allowing only devices within the facility’s geofenced perimeter to view or modify sensitive information. Geofencing technology relies on communication technologies like GPS, cellular data, and Wi-Fi to accurately define these virtual boundaries and trigger events when a device enters or exits a secure zone.
Beyond security, geofencing can also improve customer engagement by enabling location-based services and targeted alerts. For example, a company can set a geofence around its office building to control access to sensitive areas and receive instant alerts if an unauthorized device enters the geofenced area. This proactive approach not only enhances security but also streamlines compliance and operational efficiency, making geofencing an invaluable tool for businesses looking to protect their data and assets in today’s digital landscape.
Boosting the efficiency of location tracking and monitoring
Geofencing, when integrated into device tracking and monitoring, leverages GPS or RFID technology to form a virtual border encompassing a physical location, including mobile devices. Geofencing relies on accurate location data to monitor devices and enforce security policies. These virtual borders are defined based on the device's geographical location.
For IT security units, it serves as an exceptional tool, enabling them to manage and safeguard devices, no matter their location. Imagine, a protected device breaches this digital boundary, a warning can be set off, allowing for quick security actions to be taken against potential security risk. For instance, it’s possible to restrict certain device actions or activities when it’s outside the predetermined geofenced area. Such restrictions could involve blocking access to company devices, wipe data or preventing downloads of potentially harmful applications.
Triggering security actions and alerts
One of the remarkable utilities of geofencing technology is its ability to trigger specific actions or alerts. This feature can be particularly effective for IT security teams. Geofencing can trigger actions such as sending alerts or turning on security cameras to enhance security.
Customizable Alerts and Notifications
Geofencing can be configured to send alerts or notifications when a tracked device enters or exits a specific geographical boundary. These alerts or notifications can include sending a text message to users or administrators. This can give you and your team real-time insights about potential rogued behaviors that can lead to a threat. Imagine receiving an alert the moment a company device exits a secure location during curious hours – the proactive response time can be invaluable.
Actionable Insights and Responses
More than just alerts, geofencing allows IT teams to set up automated responses to certain events. If a device is detected in a risky location, you can automatically restrict its access to sensitive data or even lock the device entirely. Additionally, encrypting data can be automatically initiated to further protect user information. It can also be used to keep track of devices, helping IT teams managing and monitoring critical IT assets, offering insights into device usage patterns that could indicate potential threats or security vulnerabilities.
Common use cases of geofencing for IT operations
Activating geofences can supercharge your cybersecurity efforts and manage security systems in myriad ways. Let’s explore some practical scenarios where implementing this technology could have a significant impact.
Device management
One common use case is in device management. IT teams can establish a geofence around a specific location, such as an office or school building, and then set rules for the devices within that area. For instance, if a device leaves the geofenced area, it could be automatically locked or wiped to prevent unauthorized access to sensitive data.
Sensitive zones monitoring
Imagine creating an invisible boundary around your company’s building, server room or even cities or country. Once set up, this geofence system can alert security teams when unauthorized devices enter or exit these sensitive zones.
Enforce compliance policies
Another use case of geofencing in IT security is in the enforcement of compliance policies. For example, a company may have a policy that certain data or applications can only be accessed from within a specific geographical area. By setting up a geofence, the IT team can ensure that this policy is strictly enforced. If an attempt is made to access the data or application from outside the geofenced area, the access can be automatically denied.
Stolen device tracking
Geofencing can be particularly helpful in tracking and recovering lost or stolen devices. As soon as the device leaves a pre-defined zone, IT teams can be alerted, making retrieval attempts more timely and probable.
Location-based authentication
Geofencing can be used to provide location-based authentication. This means that a user’s current location can be used as an additional factor in the authentication process. For example, if a user typically accesses a system from a specific location, and then suddenly attempts to access it from a different location, this could be flagged as suspicious and require additional authentication.
Prey's device tracking and geofencing capabilities
Prey’s device tracking solution uses geofencing to monitor if your device is in permitted areas, prompting you with an alert if it has left the geofenced area, warning you that something is wrong. Since a geofence is an area with virtual boundaries or perimeter on a virtual map, GPS tracking tells us in real-time data when a device goes in or out of the established perimeter.
With geofencing, Prey's solution offers a new and efficient method to track and protect your remote devices, providing meaningful benefits for your IT team.
Benefits of utilizing Prey for tracking and geofencing
Prey shines as an all-in-one device security solution that can provide just the right tools for this job. At the core of Prey's geofencing solution is the ability to construct virtual perimeters anywhere across the globe. Home offices, remote workspaces, or even public places can all be transformed into protected areas in no time. If any device breaches these barriers, immediate alerts are triggered to quickly prevent any possible data breaches or device loss.
Let's dive into Prey's geofencing details:

Proactive Alerts: Prey’s geofencing feature can be set up to send alerts when devices enter or leave the geofences. This will keep the business' IT team informed about any unexpected user movements, helping them maintain a tight rein over the organization's devices.
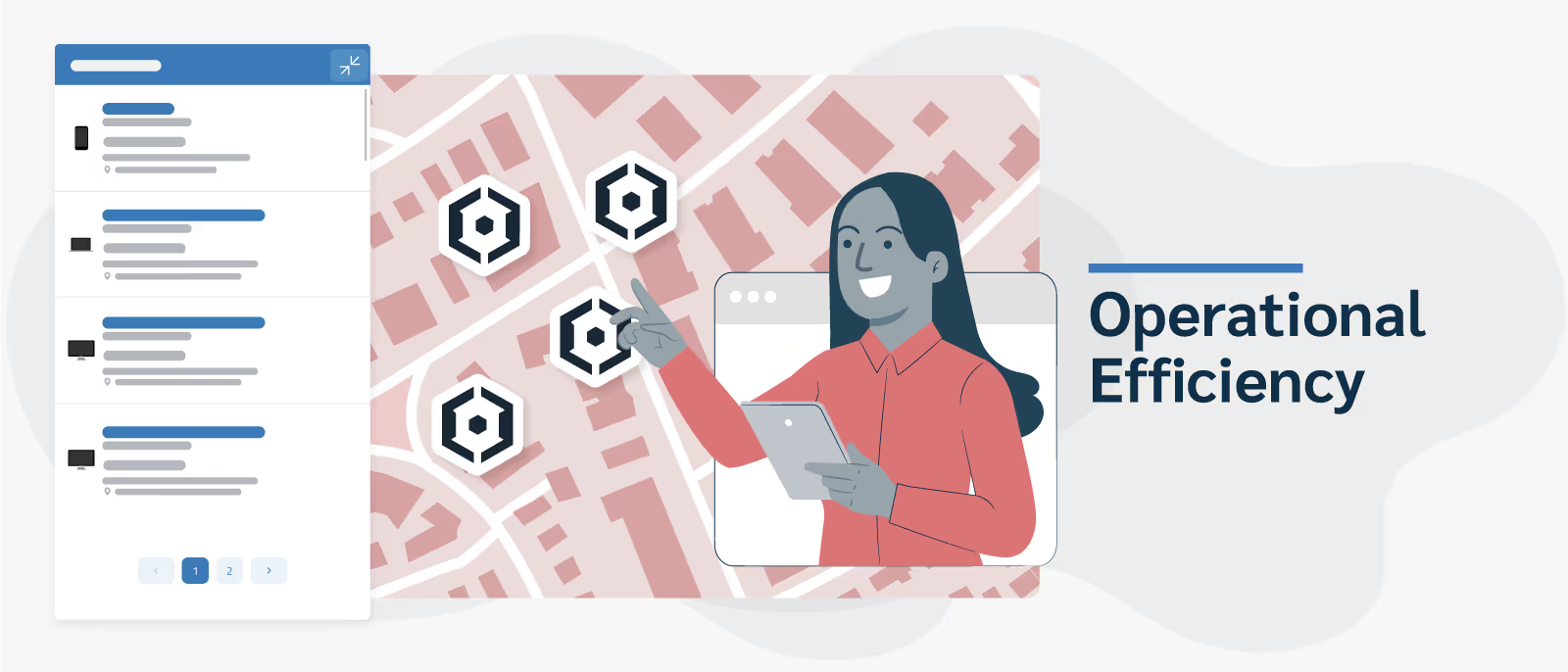
Operational Efficiency: Prey's global fleet and location tracking feature lets you visualize the location of all your devices at the same time on a map. This kind of real-time monitoring and location tracking helps ensure none of the devices fall off the radar, leading to an efficient supervision of the entire fleet.
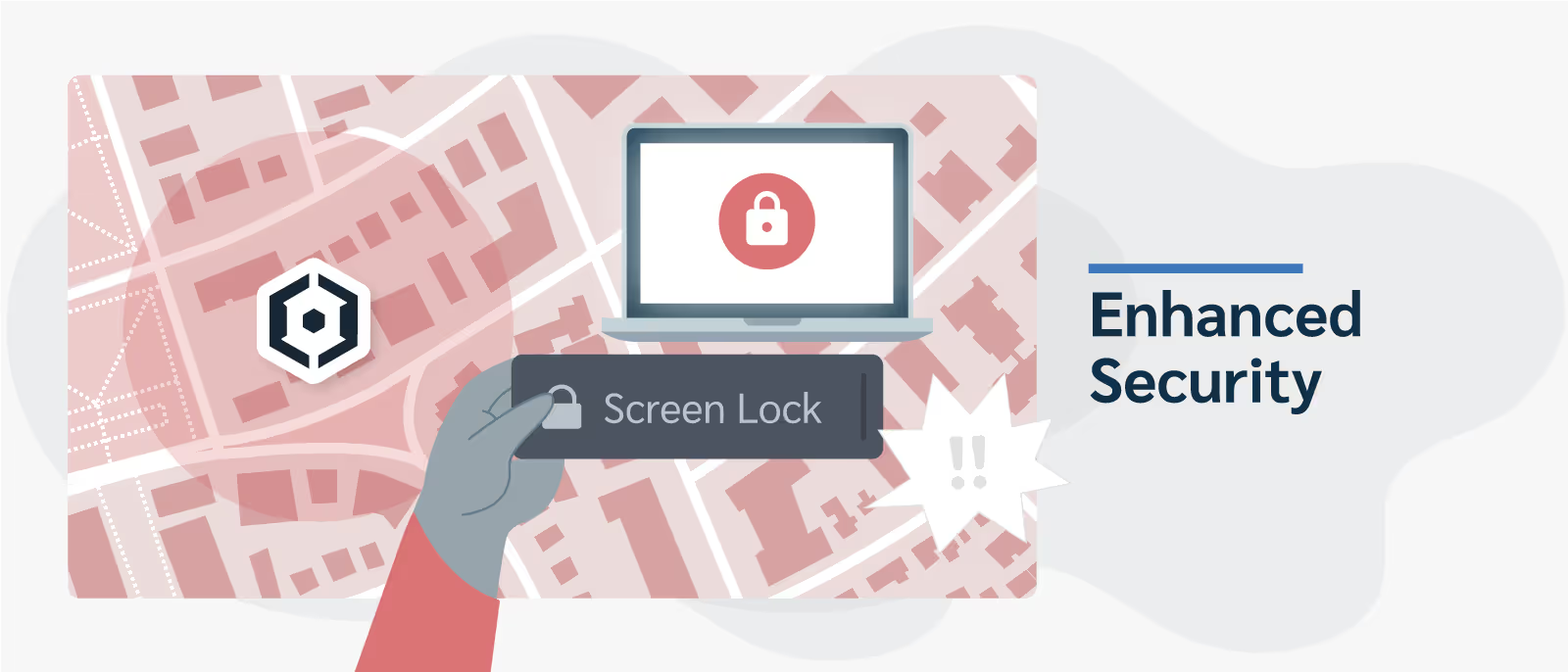
Enhanced Security: Prey's screen lock feature is another useful security measure. If a device is suspected to have been compromised or misplaced, it can be blocked remotely, ensuring that unauthorized apps or users can't access the device.
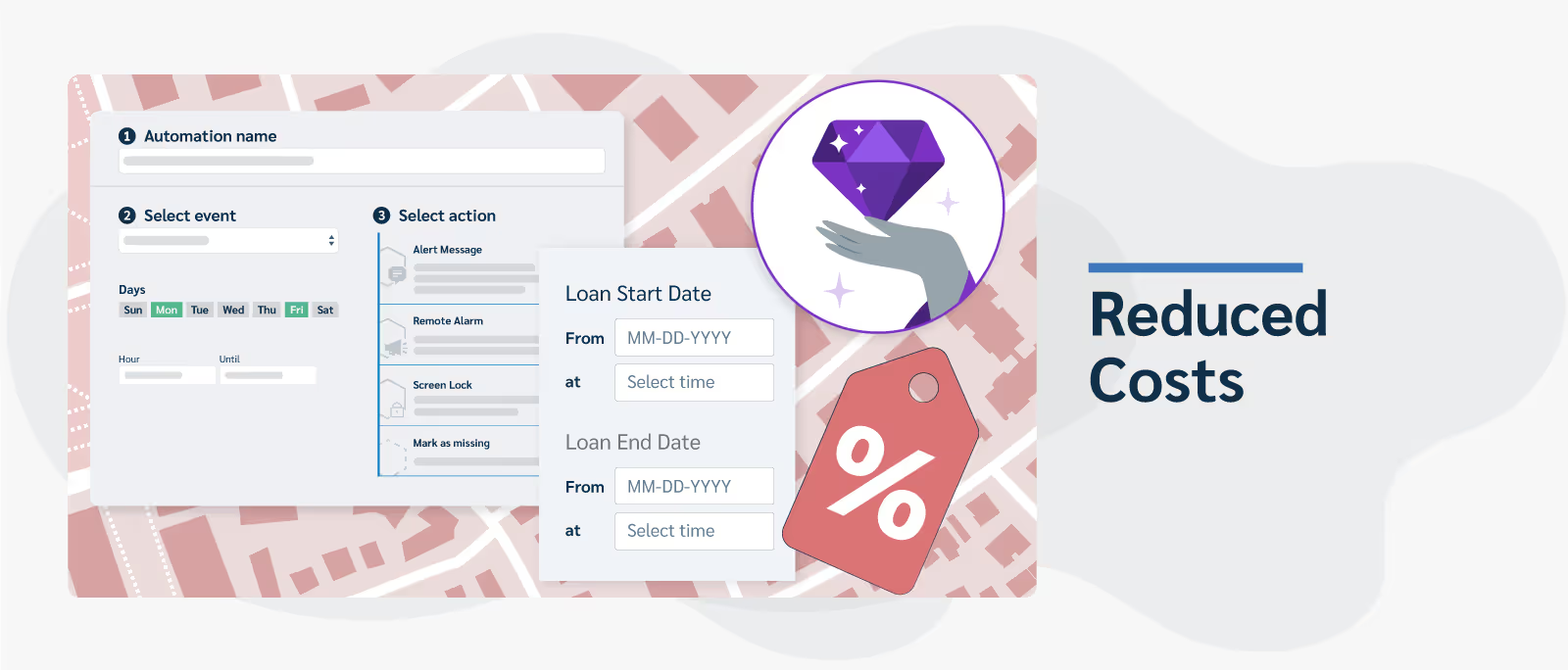
Reduced Costs: Prey's geofencing capability comes as part of their full suite service plan, which includes a host of other features like device loan management and custom automation. This allows for the efficient use of resources and, in turn, leads to significant cost savings.
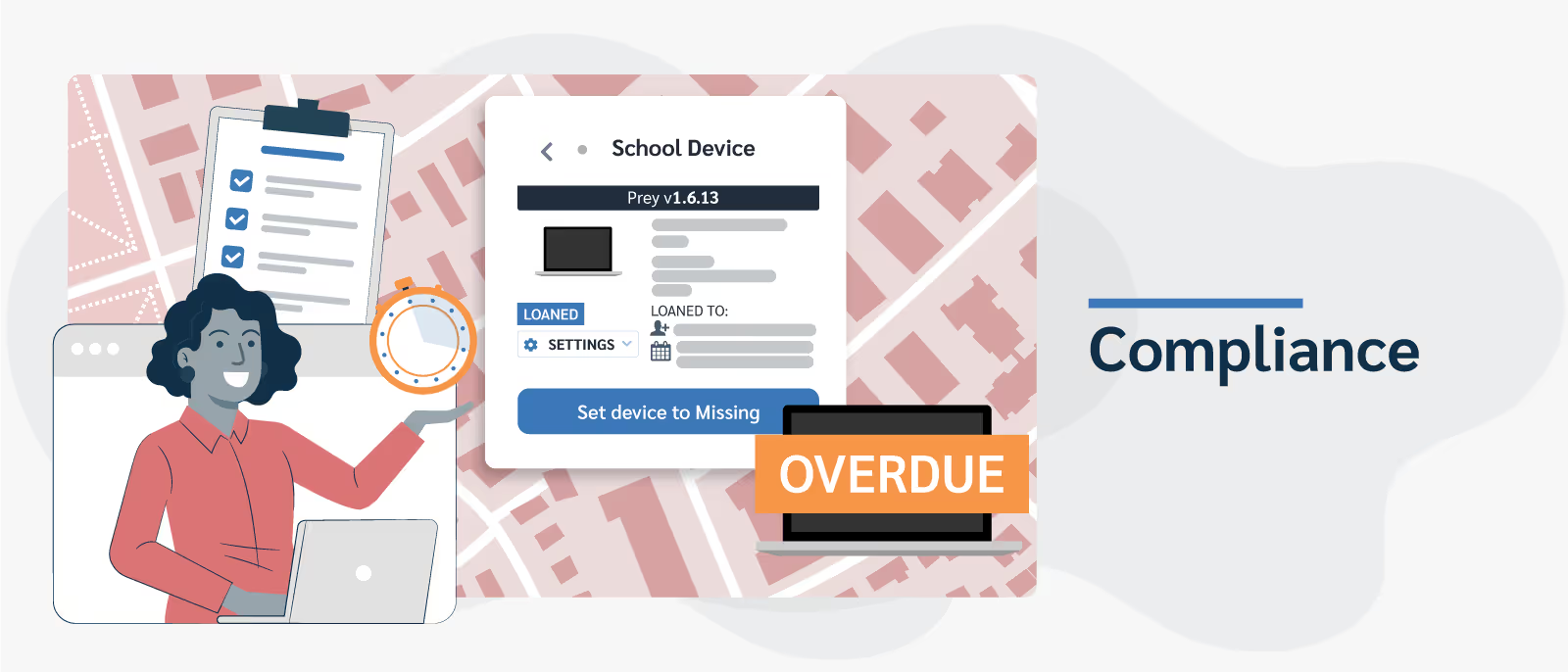
Compliance: Through Prey’s inventory management features, you can assign users, create and setup device loans with return dates, and activate security measures when due dates are overdue. This helps to control access and ensure devices are only used by authorized personnel and within the right context, thus aiding compliance.
Essentially, Prey's geofencing software solution puts power back into the hands of your IT teams, empowering them to develop robust, location-based security protocols. With this software solution, IT security has never been easier nor more effective.
Conclusion
With all factors considered, the role of geofencing in cybersecurity is impossible to ignore, shaping a future where IT security becomes even more proactive and less reactive. By integrating geofencing capabilities into device tracking, monitoring, and security solutions, IT teams can generate an environment that is not only secure but also efficient and effective.
By employing geofencing solutions like those offered by Prey, companies can fortify their cybersecurity, minimize risks, and assure the protection of their valuable assets. We conclude that geofencing, in essence, invites IT teams to redefine their strategies and embrace a more empowered stance toward cybersecurity.





