Device tracking and inventory management
Know exactly where your company devices are, always
Track all company devices, their status, and manage their lifecycle from one dashboard. With Prey, you get peace of mind and total operational oversight.
Struggling to keep up with your devices?
Stop inventory chaos
Quit the endless search. Prey gives you an accurate record of all your devices in real time, so you always know what you have and who has it.
Close security gaps
Prey protects your devices and data with always-on location services and remote security tools. Make sure that no device poses a risk to your company.
Automate tasks efficiently
Free your team from manual audits. Prey let's you plan ahead, automate actions and save time to focus on more strategic tasks.
Prioritize compliance
Unknown device locations and users can lead to compliance violations for your organization, particularly when sensitive data is involved.
The Prey solution:
Simplified device inventory and tracking
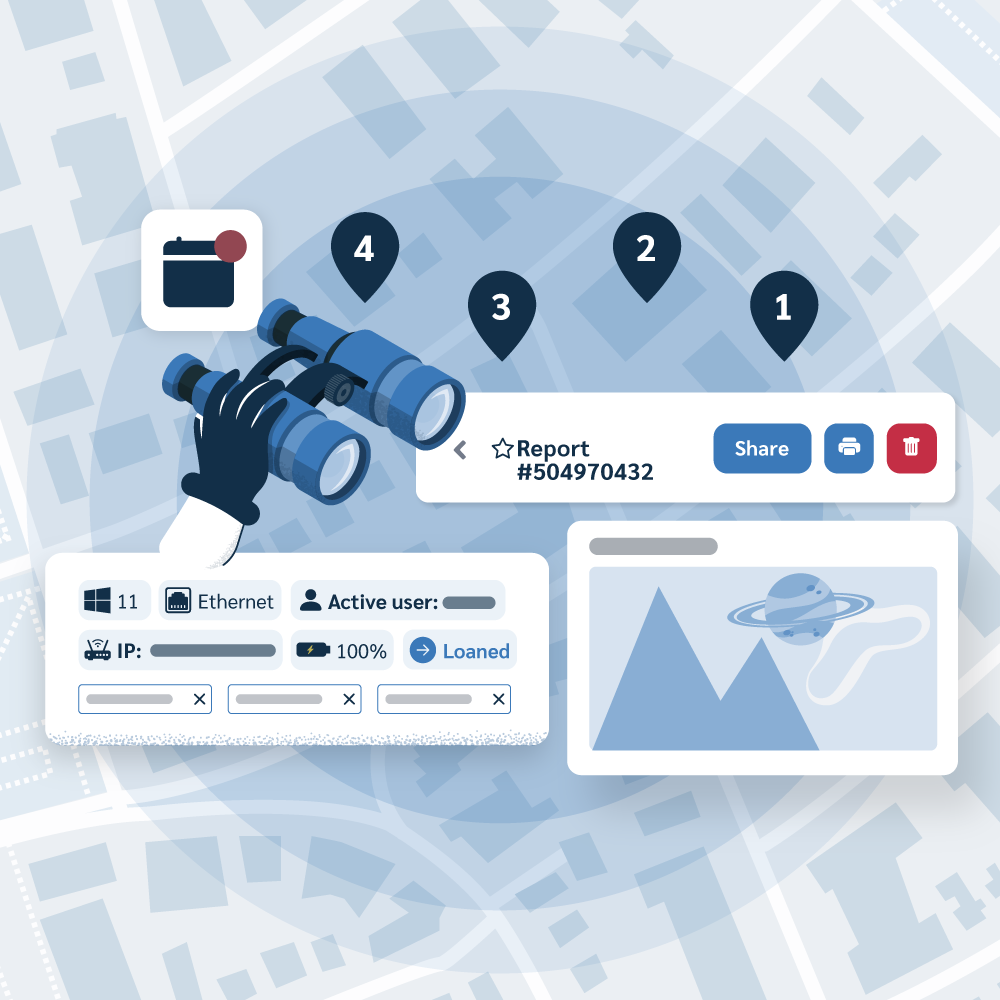
Your entire fleet at a glance
Visualize your device locations on a map, assign users, and take action, all from one intuitive control panel. Watch a Demo to see it in action.
Explore more
Keep remote devices visible and secure. Learn why device tracking matters for remote teams, how it supports compliance, and how Prey helps protect endpoints anywhere.

This document highlights the challenges of managing rental devices and how Prey offers solutions like remote security, automated tracking, and compliance features.
Frequently asked questions
Below, you'll find answers to commonly asked questions about our products/services. Feel free to reach out to us directly for further assistance. We're here to help!
Prey is a multi-platform solution that works on a wide range of devices. This includes laptops (Windows, macOS, Ubuntu), smartphones and tablets (Android, iOS), and even Chromebooks. As long as a device can run our agent, you can track it.
Prey uses a combination of technologies for location tracking, depending on the OS in question. We use GPS, Wi-Fi triangulation, mobile data and sometimes a mix of them. Android and iOS rely on GPS being on. Windows relies on triangulation and requires the Wi-Fi adapters to be turned on. This multi-layered approach ensures that you can locate a device even if GPS is off or unavailable, providing the most accurate location possible.
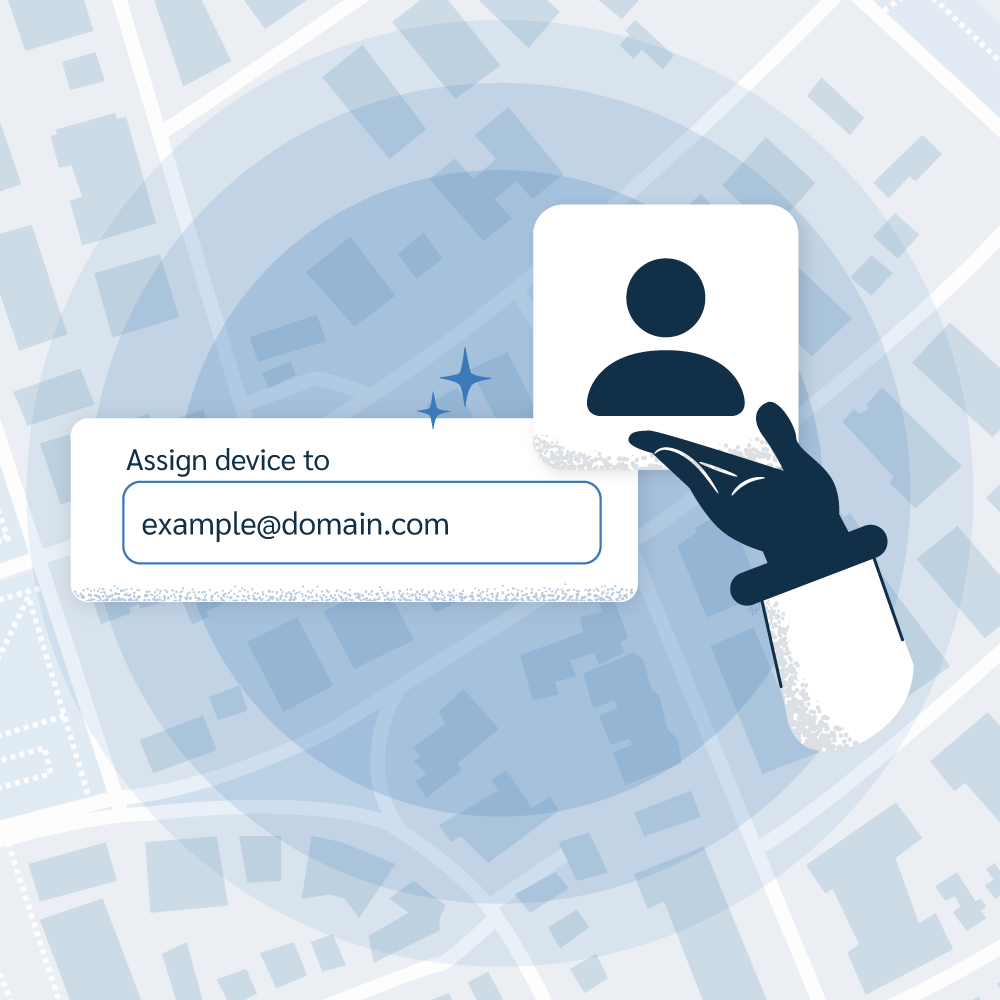
While Prey is renowned for its location and recovery features, it has enough device and user management features to be a well-rounded administration solution. Our platform is designed to help manage and take inventory of devices. You can use it to know which employee has which device, see its hardware status, and manage your entire fleet, even when devices are safe and in use.
Our dashboard gives you a comprehensive view of your device fleet. You can see crucial details like:
- Auto-updating map location
- Assigned user
- Custom labels
- Hardware information (RAM, CPU, storage)
- Network connections
- Device health (battery level, last connection time)
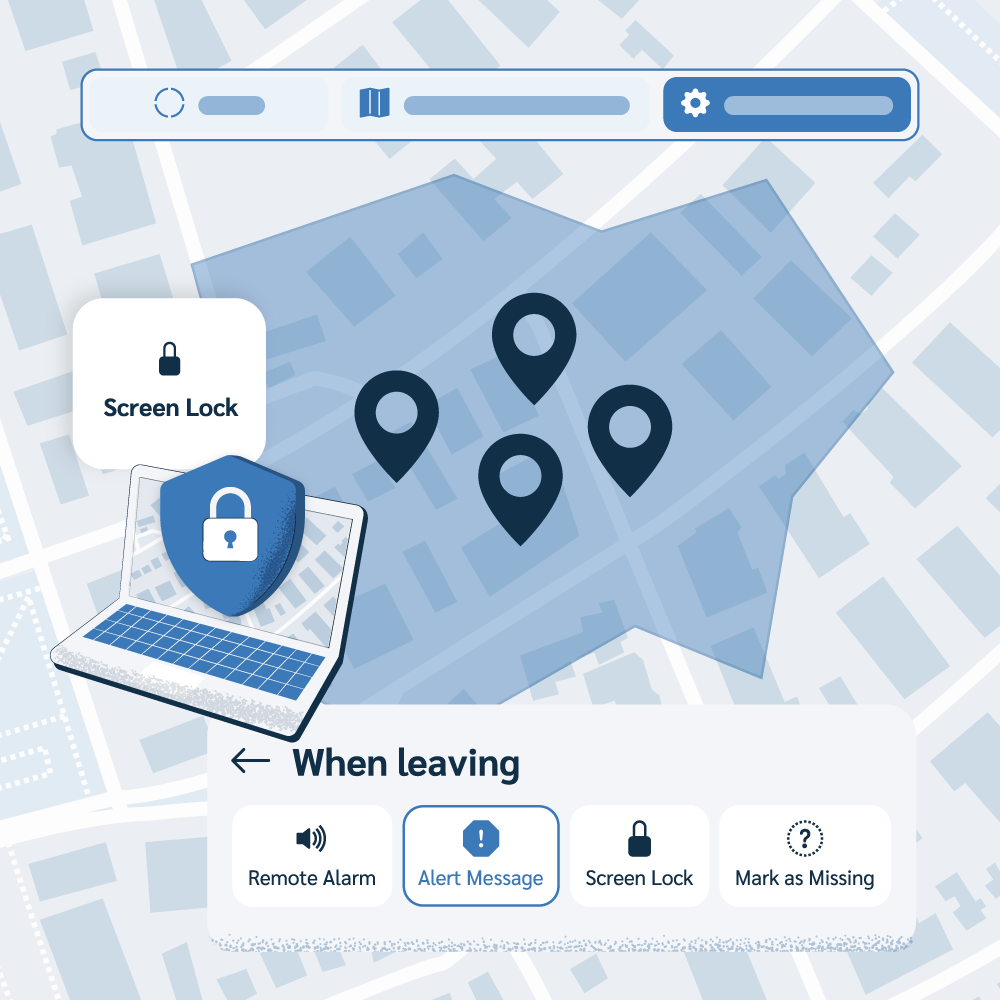
Prey's capabilities extend beyond location. You can remotely perform actions to secure your devices. This includes:
- Remote Lock: Instantly lock a device to prevent unauthorized access.
- Data Wipe: Erase sensitive data from a device to protect company information.
- Geofencing: Set up virtual location boundaries and automatically trigger actions (like a notification or lock) if a device enters or leaves a specific area.
Yes. Prey is designed for scalability and ease of use. You can quickly enroll devices in bulk and manage them all from a single, intuitive dashboard. We also offer dedicated support to help you with the onboarding process and ensure a smooth integration into your existing IT workflow. Prey also has app packages available for mass MDM deployment.