Device rental security
Protect your rental devices. Protect your business
In device rental, inventory is paramount. Lost or unreturned devices impact profitability and security. Prey tracks and protects your rental fleet, safeguarding assets and your bottom line.

The unique risks of the device rental model
Lost or unreturned inventory
A significant portion of your capital is tied up in devices. When a client doesn't return a device or it goes missing, it's a direct loss to your business.
No real-time visibility
It's a huge logistical challenge to know where every leased device is at any given moment, making it impossible to audit your assets or respond to a problem in real time.
Risking your customer's data
Devices in a rental fleet can contain sensitive client data. If a device is lost or not properly wiped upon return, it creates a major security and liability risk. Treading carefully with third-party privacy is a must.
Manual tracking doesn't scale
Managing thousands of devices and their rental status is time-consuming and prone to human error, creating a bottleneck for your ops team.
The Prey solution:
Total control for your rental fleet
Your rental fleet, at a glance
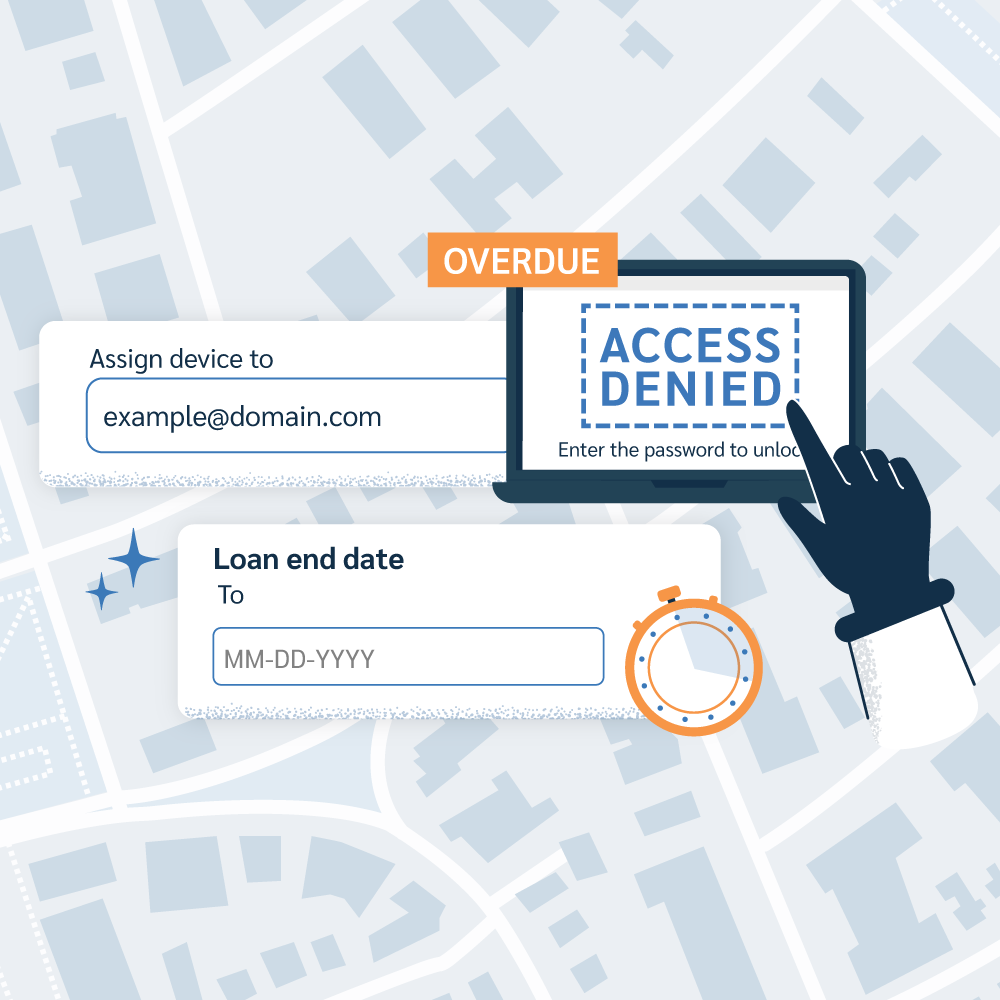
The Prey Panel is your command center for DaaS management. Visualize every leased device on a map, see its loan status, and take action with a single click. This powerful, intuitive overview gives you the control and peace of mind you need to run your business with confidence.
Explore more

Remote work expands your attack surface. Learn the essential controls—MFA, encryption, endpoint protection, MDM, and lost device response—to stay secure.

This document highlights the challenges of managing rental devices and how Prey offers solutions like remote security, automated tracking, and compliance features.
Frequently asked questions
Below, you'll find answers to commonly asked questions about our products/services. Feel free to reach out to us directly for further assistance. We're here to help!
Loan Manager is a dedicated tool that fits great with DaaS providers. It allows them to track which client has which device and for how long. From a single dashboard, you get a clear overview of every active loan, helping you maintain accurate records and a clear chain of accountability for all your leased assets.
Prey gives you the critical tools to enforce contract compliance remotely. If a client defaults on payments or violates the agreement, you can use mass Screen lock to instantly block access to the devices and prevent further use. This protects your assets and provides leverage for contract resolution. You can also wipeor return devices to factory settings to eliminate liability and protect any sensitive data before attempting retrieval. If the device is simply missing, you can use our location tracking and detailed reports to pinpoint its location and initiate recovery.
Geofences provide an extra layer of automated security. You can create boundaries around a client's work site or your own warehouse. If a device leaves its designated zone, you can set up notifications and trigger Geofence actions like Screen lock. You may also flag them to receive Missing reports that contain location information, photos and screenshots, and general device/user information.
Prey gives you full control to secure devices even when they are in a client's possession. You can remotely lock the screen to prevent access or trigger remote encryption to protect sensitive data. You can even Factory reset devices from your own device anywhere, anytime. This ensures your assets and your clients' information remain secure throughout the lease agreement.
Yes. Wipe devices clean remotely, and then perform unattended installations for bulk, zero-touch deployment. This streamlines your device preparation process to quickly get new devices ready for your clients while making sure they are secured and managed from the moment they are leased.
Prey is much more than a simple location tracker. We provide an end-to-end solution for DaaS and rental management. This includes Always-on, 24-7 location tracking, but also automated security actions, asset organization tools like labels and groups, a dedicated Loan manager service, and remote data protection features to provide a comprehensive solution for your business.