What is data security?
Data security is the practice of protecting digital information from unauthorized access, corruption, or theft throughout its entire lifecycle. It encompasses a wide range of strategies and technologies—such as encryption, access controls, endpoint protection, and data loss prevention (DLP)—to ensure the confidentiality, integrity, and availability of sensitive data.
Today, data security isn’t just about protecting corporate information—it’s also about safeguarding customer, employee, and partner data across increasingly complex environments, including cloud infrastructure, hybrid work models, and BYOD (Bring Your Own Device) setups.
The scale of the challenge continues to grow. According to Surfshark’s Data Breach Statistics (2024), over 300 million data records were exposed globally in 2023—an alarming 72% increase from the previous year. These breaches range from small incidents in local government offices to massive attacks, such as the MOVEit Transfer hack, which impacted hundreds of organizations worldwide and compromised sensitive personal and financial data.
Why is data security necessary?
Strong data security is essential to protect against both financial and reputational damage caused by data breaches. In today’s threat landscape, no organization is immune—making security not just an IT issue, but a business-critical priority.
According to IBM’s 2023 Cost of a Data Breach Report, the average global cost of a data breach has reached $4.45 million, a 15% increase over the past three years. The report highlights four key cost areas:
- Detection and escalation: 29%
- Post-breach response: 27%
- Notification costs: 6%
- Lost business and reputational damage: 38%
What’s especially concerning is the long-term impact of lost trust. IBM found that breaches involving customer data have the highest churn rates, especially in industries like healthcare and finance.
Beyond financial costs, failing to secure sensitive data can result in severe regulatory consequences. Global frameworks like GDPR, HIPAA, CCPA, and PCI-DSS impose strict requirements—and fines can reach up to 4% of a company’s annual global turnover under GDPR alone. Even without a breach, non-compliance can lead to penalties, lawsuits, and loss of business operations (e.g., losing the ability to process card payments under PCI-DSS).
In short, data security is no longer optional. It’s the foundation for customer trust, legal compliance, and long-term operational resilience.
Types of data security
The objective of data security is to protect sensitive data by minimizing the probability that it will be leaked or exposed to unauthorized users.
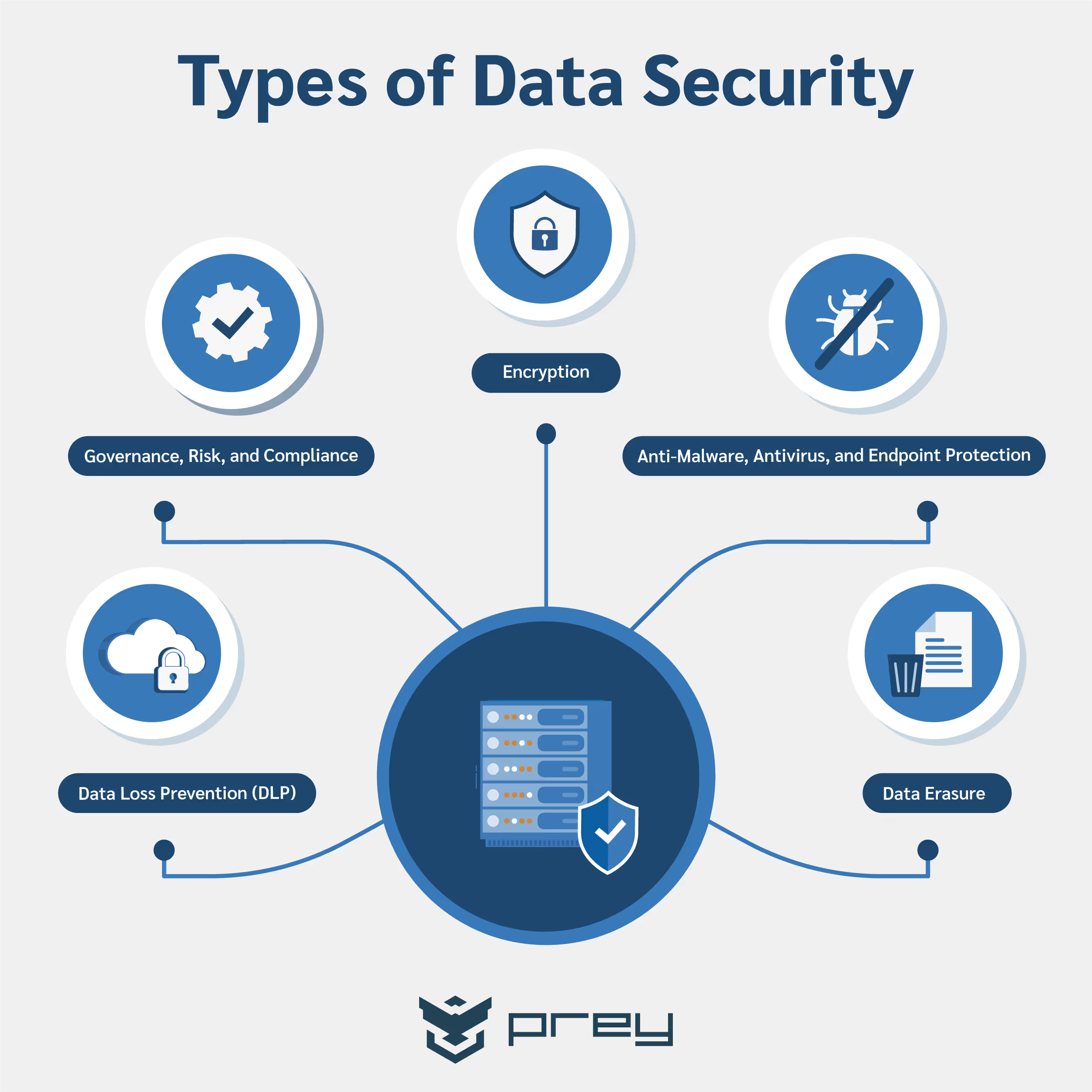
A number of different tools exist for achieving this goal, including:
Encryption
Encryption algorithms make it impossible to read data without access to the proper decryption key. Encrypt data using cryptographic keys to ensure secure sharing and protect personal information on removable storage devices like USB drives and SIM cards. Under many data protection laws, if encrypted data is leaked, but the attacker does not have access to the decryption key, the breach does not need to be reported.
Prey can manage BitLocker for Windows 10 devices with a physical Trusted Platform Module (TPM) installed and active. With it, you can select which disks to encrypt and decrypt, check on their progress and use the security standard that best suits your needs.

Data erasure
It is the process of securely deleting sensitive data from storage devices such as hard drives, USB drives, and mobile devices. However, when data is wiped, it is frequently not entirely erased from the device and can sometimes be recovered using special software.
Data erasure involves overwriting the existing data with random characters or zeros to make it unrecoverable, preventing unauthorized parties from accessing sensitive data and helping protect against data security threats. Data erasure policies and processes should be implemented mainly by organizations handling sensitive data to prevent data breaches.
Identity access management (IAM)
Access control systems enable an organization to limit users’ access and permissions to the minimum required for their job role (the principle of least privilege) and to manage who can access data within digital environments. Implementing IAM decreases the probability and impact of data breaches and is required for compliance with certain data protection regulations (such as PCI-DSS).
Data loss prevention (DLP)
DLP solutions are designed to identify and alert on or block attempted data exfiltration from an organization’s network. These systems can be a good last line of defense against data breaches but are most effective when paired with other solutions. They might miss an attempted exfiltration and only come into play once an attacker has already gained access to an organization’s data.
Governance, risk, and compliance
Policies and risk assessment procedures are essential for a robust data security strategy. By defining policies regarding data classification, access, and protection for different data types, an organization can reduce its risk of a data breach.
Anti-malware, antivirus, and endpoint protection
Many data breaches are enabled by malware, including ransomware that steals data to force a victim to pay a ransom or info stealer malware that steals users’ credentials and data. Installing anti-malware, antivirus, and endpoint protection solutions on devices can help to detect and block attempted data theft by malware.
While various solutions exist for implementing data security, different approaches are better at managing different risks. For example, lost or stolen devices have been the source of numerous data breaches. While IAM and DLP solutions have little impact to prevent these types of incidents, they can alert IT employees of any unauthorized behavior and prevent any data leaks by deploying full-disk encryption, device lock, or remote wipe on devices carrying sensitive company or customer data, which can help to mitigate these threats.
Data security threats
Data is everywhere within an organization’s network, and it can be put at risk in a number of different ways. Some top threats to data security include
- Data Loss in the Cloud: Many organizations are moving to the cloud, but cloud security has consistently lagged. 60% of cloud storage includes unencrypted data, and security misconfigurations in 93% of cloud storage services have caused over 200 data breaches in the last two years. Since these cloud-based resources are directly accessible from the public Internet, this places the data they contain at risk.
- Phishing and Other Social Engineering Attacks: Phishing and social engineering attacks are common methods for stealing sensitive data. A malicious email, SMS, social media message, or phone call may attempt to steal sensitive information directly or steal user credentials. These credentials can then access online accounts containing sensitive information, such as cloud-based email or data storage.
- Accidental Exposure: Not all data breaches are intentional. According to IBM and the Ponemon Institute, 48% of data breaches are caused by system glitches or human error. This can include everything from an accidental CC on an email to misconfiguring cloud security permissions to leaving a USB drive or printout on the subway.
- Insider Threats: The popular conception of data breaches is that outside attackers mainly carry them out. However, insider threats are behind an estimated 60-75% of data breaches. This includes both malicious insiders – like rogue employees that still have access to the network – and negligent employees that cause accidental data exposures.
- Ransomware: Ransomware is a threat to an organization’s data in a couple of different ways. All ransomware variants perform data encryption, which makes the data impossible to access without paying the ransom for the decryption key. Some ransomware groups have added a data stealer to their malware, which provides additional leverage when demanding a ransom payment.
- Physical Hardware Compromise: All data is stored on physical hardware, which may be the attack's target. . Malicious hardware inserted via a supply chain attack can compromise sensitive data, or an attacker can attempt to read memory directly off of a disk while it is still turned off.
- Stolen/missing devices: Working from anywhere can lead to cybersecurity risk since Devices and their sensitive data may get stolen or lost. These devices frequently hold private data that unauthorized people can access if they fall into the wrong hands, including emails, financial information, personal files, and access credentials to company networks and databases which can lead to a serious data breach.
How to improve data security at your workplace
Many data security decisions are made at the executive level, such as corporate policies and the security solutions to deploy to protect the business. However, there are simple steps that you can take to improve your own data security and that of the business, including:
- Use Strong Access Control: Weak passwords are one of the biggest cybersecurity threats to an organization and its data. Use strong, unique passwords for all accounts and turn on multi-factor authentication (MFA) wherever available. Also, Identity Access Management (IAM) tools help to ensure that only authorized users can access specific resources. IAM tools include user authentication, authorization, and administration, enabling administrators to manage access, monitor user activity; and revoke access when necessary. Enterprises can use IAM tools to improve access control procedures, lower the risk of data breaches, and prevent unauthorized access to sensitive data.
- Install Full-Disk Encryption: Full-disk encryption stores data in an encrypted state, making it impossible to read without the proper password. This protection against physical attacks grows more important as working from mobile devices becomes more common.
- Share Data Securely: Using sharing links for cloud-based documents and data makes them accessible to anyone with the link, and tools exist specifically to search for these links. Send an individual invite to access the resource rather than turning on link sharing.
- Create Backups Regularly: Ransomware is a serious threat, and a successful attack can cause significant data loss. Set up an automatic backup solution to make a copy of data to read-only storage to protect against these attacks.
- CyberSec Training: User awareness is essential to the success of enterprise data security. Check out this blog for tips on developing cybersecurity awareness training for employees.
- Risk Assessment check-ups: It’s a proactive method of identifying and reducing security risks that could result in unauthorized access to data. It involves reviewing the security measures in place at a business, looking for weaknesses, and determining the risk and potential consequences of a security breach. This process helps organizations understand and identify where security measures need improvement.
- Create and Execute a Comprehensive Data Security Plan: A data security strategy is critical for securing sensitive information and ensuring that staff understands their role in security. Regular data backups, encryption mechanisms, access control rules, incident response processes, and employee training on security best practices should all be included in this strategy. A well-designed data security plan may aid in the prevention of data breaches and the reduction of the effect of security events.
Data security best practices
Create a data security policy
A data security policy is a cornerstone of any robust data security strategy. It serves as a comprehensive guide for protecting sensitive data and preventing data breaches. This policy should cover several key areas:
- Data Classification: Define categories for different types of data based on their sensitivity and importance. This helps in applying appropriate security measures to each category.
- Access Control: Outline who has access to what data and under what circumstances. Implementing role-based access control ensures that employees only access the data necessary for their job roles.
- Data Encryption: Specify the encryption standards and practices to be used for protecting data both at rest and in transit.
- Data Loss Prevention: Include measures and tools to detect and prevent unauthorized data transfers or leaks.
Additionally, the policy should clearly define the roles and responsibilities of employees in safeguarding sensitive data. Regularly reviewing and updating the data security policy is crucial to adapt to new threats and ensure its effectiveness.
Implement access control
Access control is a fundamental aspect of data security, ensuring that only authorized individuals can access sensitive data. Implementing robust access control measures can significantly reduce the risk of data breaches. Here are some key practices:
- Multi-Factor Authentication (MFA): Require multiple forms of verification before granting access to sensitive data. This adds an extra layer of security beyond just passwords.
- Role-Based Access Control (RBAC): Assign access permissions based on job roles. This ensures that employees only have access to the data necessary for their duties.
- Network, Application, and Data Level Controls: Implement access control measures at all levels to provide comprehensive protection.
Regularly reviewing and updating access control measures is essential to address new vulnerabilities and ensure they remain effective. By doing so, organizations can better protect sensitive data and prevent unauthorized access.
Use strong passwords
Strong passwords are a basic yet critical component of data security. They help prevent unauthorized access to sensitive data. Here are some best practices for creating and managing strong passwords:
- Length and Complexity: Passwords should be at least 12 characters long and include a mix of uppercase and lowercase letters, numbers, and special characters.
- Regular Changes: Change passwords regularly, ideally every 60 to 90 days, to minimize the risk of them being compromised.
- Unique Passwords: Avoid reusing passwords across multiple accounts or systems. Each account should have a unique password.
- Password Managers: Use a password manager to generate and store complex, unique passwords securely.
By following these practices, individuals and organizations can significantly enhance their data security and protect sensitive information from unauthorized access.
Regularly Update and Patch Systems
Keeping systems updated and patched is vital for maintaining the security of sensitive data. Updates and patches often include critical security fixes that address vulnerabilities and prevent data breaches. Here are some key points to consider:
- Timely Updates: Regularly update all software, applications, and operating systems to ensure they have the latest security patches.
- Automated Updates: Where possible, enable automated updates to ensure that systems are always up-to-date without manual intervention.
- Review and Patch: Regularly review systems for any missed updates or patches and apply them promptly.
Failing to update and patch systems can leave them vulnerable to exploitation by hackers. By keeping systems current, organizations can protect sensitive data and reduce the risk of data breaches.
By following these data security best practices, organizations can help protect sensitive data and prevent data breaches. Implementing a data security policy, access control, strong passwords, and regularly updating and patching systems are all critical components of a comprehensive data security strategy.
How to improve your data security strategy at your workplace
Many data security decisions are made at the executive level, such as corporate policies and the security solutions to deploy to protect the business. However, there are simple steps that you can take to improve your own data security and that of the business, including:
- Use Strong Access Control: Weak passwords are one of the biggest cybersecurity threats to an organization and its data. Use strong, unique passwords for all accounts and turn on multi-factor authentication (MFA) wherever available. Also, Identity Access Management (IAM) tools help to ensure that only authorized users can access specific resources. IAM tools include user authentication, authorization, and administration, enabling administrators to manage access, monitor user activity; and revoke access when necessary. Enterprises can use IAM tools to improve access control procedures, lower the risk of data breaches, and prevent unauthorized access to sensitive data. Be especially cautious with personal or financial information to avoid falling victim to impersonators.
- Install Full-Disk Encryption: Full-disk encryption stores data in an encrypted state, making it impossible to read without the proper password. This protection against physical attacks grows more important as working from mobile devices becomes more common.
- Share Data Securely: Using sharing links for cloud-based documents and data makes them accessible to anyone with the link, and tools exist specifically to search for these links. Send an individual invite to access the resource rather than turning on link sharing.
- Create Backups Regularly: Ransomware is a serious threat, and a successful attack can cause significant data loss. Set up an automatic backup solution to make a copy of data to read-only storage to protect against these attacks.
- CyberSec Training: User awareness is essential to the success of enterprise data security. Check out this blog for tips on developing cybersecurity awareness training for employees.
- Risk Assessment check-ups: It’s a proactive method of identifying and reducing security risks that could result in unauthorized access to data. It involves reviewing the security measures in place at a business, looking for weaknesses, and determining the risk and potential consequences of a security breach. This process helps organizations understand and identify where security measures need improvement.
- Create and Execute a Comprehensive Data Security Plan: A data security strategy is critical for securing sensitive information and ensuring that staff understands their role in security. Regular data backups, encryption mechanisms, access control rules, incident response processes, and employee training on security best practices should all be included in this strategy. A well-designed data security plan may aid in the prevention of data breaches and the reduction of the effect of security events.
Data security regulations
Data protection regulations have been around for many years. However, in the last few years, the regulatory landscape has grown very complex very quickly.
The exact data privacy laws an organization must comply with depend on its location and industry. Some major data security regulations to be aware of include:
General data protection regulation (GDPR)
The GDPR was passed in 2016 and went into effect in 2018. It protects the personal data of EU citizens and applies to any organization with EU customers, regardless of location. The GDPR kicked off the recent surge in data privacy laws, inspiring many of them.
Health insurance portability and accountability act (HIPAA)
HIPAA is a US regulation that protects the personal health data of US citizens. Its data security requirements apply to healthcare providers and their service providers who may have access to data protected under the law.
Federal information security management act (FISMA)
FISMA is a law governing information security for the US government. It codifies the cybersecurity and data security protections and policies federal agencies must make.
Sarbanes-Oxley act (SOX)
SOX is a law designed to protect investors in a company against fraud. Data security is an important component of this, as a data breach can hurt the value of a company’s stocks. After the Solarwinds hack, a class-action lawsuit was filed against the company, asserting its claims regarding cybersecurity in its SOX filings were untrue and misleading.
Data security vs. data privacy
Data privacy and data security are crucial components of safeguarding sensitive data, but they deal with different issues.
Data security is safeguarding information against unauthorized access, theft, destruction, or alteration. To prevent unwanted access and guarantee the confidentiality, integrity, and availability of data, entailing security controls like encryption and monitoring.
Data privacy is the term used to describe a person's right to control how their personal information is gathered, utilized, and shared. It includes preventing unauthorized disclosure or misuse of a person's personal information.
In conclusion, the main difference is that data privacy focuses on defending a person's right to own their personal information and keep their data confidential. In contrast, data security takes action to prevent unwanted access to said data, protecting it from malicious activity. When handling sensitive data, both are crucial factors for organizations to consider, as failing to do so may have a negative legal and financial impact on the brand.
Data security takeaways
Data security is an ongoing process vital for individuals and organizations to maintain the integrity and confidentiality of their data; keeping on top of changing threats and vulnerabilities requires constant monitoring, upgrading, and training. Therefore, it is essential to develop a data security plan and keep it updated to ensure it complies with your business’s evolving needs and legal regulations to prevent data breaches. For more information, you can refer to our data security faqs.
Data security is not a one-size-fits-all solution. Instead, it requires a customized approach based on each organization’s unique needs, risks, and challenges. Every person can contribute to data security through cyber hygiene, which involves using strong passwords, avoiding public Wi-Fi networks, and being vigilant for phishing scams.




