Picture this: you’re looking for software to help you track devices, and you found us. You’re interested in taking care of your devices (or the ones of your clients) and starting a trial of our service. Maybe you have a small fleet of different laptops & mobiles or a huge one to be taken care of. For all of those possibilities, you may be wondering how to start. And we’re here to help you!
No matter how large or small your fleet is (or how different), you would have to follow the same steps to protect your devices to the maximum capacity. This article will help you to get a clean start and to optimize our platform to be used as a device tracker. So let’s get to it!
Why you should use Prey for device tracking
But wait a minute… I don’t really know Prey that much!
Let’s get acquainted, then! Prey is a subscription-based device security service that delivers location, data protection, and multi-platform device management for individuals and organizations that need to secure devices. We provide stellar device tracking and an easy user interface, which helps our users keep control and simplify the management of their fleets, large or small.
Prey can work as a standalone app or in tandem with any endpoint security solution or MDM. We provide a secondary layer of protection with apps like Intune or JAMF, improving your tracking capabilities.
Good to know, but I’m an MSP… Do you have a solution for me too?
Great question! Our solution for Managed Service Providers is tailored to deal with multiple clients to deliver specific solutions. Acting as a sort of "omni-Prey" through a multi-tenant platform, you can manage several instances of Prey for all your clients, with separate dashboards, unattended installations, and different policies for everyone. You have complete control.
Okay, I get it. Prey is a tracking & management suite with device protection features, that works well with others, and has a specific MSP solution. But why should we use it?
Prey excels in a lot of business & organizational environments that need a dedicated device location tool. Some examples include, but are not limited to:
- When a location tracking tool is needed for compliance, such as NIST 800-53
- When endpoint management solutions don’t have location services, or when those solutions are basic and on-demand (i.e. when using Hexnode, Meraki, Sophos, and others)
- When you need a secondary location tool that doesn’t require a lot of resources from every machine to run properly
- When your clients don’t require a potent MDM solution, just one for device inventory and location management
- When the price is a major issue (we’re more affordable, and the price goes down the more slots for devices you add!)
In summary, if you need a tool that can handle a small or large inventory, that has leading location tracking, with huge data protection and management capabilities, we’re a perfect match.
Before we begin…
To start using Prey to its fullest potential, you have to be ready. Here’s a list of things you may do to get started:
- OPTIONAL: Are you using or trying Prey for MSP? To start, you would have to create a client to host your Prey Panel. Only when a client is created and slots are assigned, you can enter the Panel for that specific client. If you are just using one of our enterprise plans, skip this step
- Have you added devices to your account? Starting from one device you can try everything, but Prey excels at large fleets. Don’t have time to install them all manually? Use our unattended installation process, or install us through an MDM
- Note: Prey uses Wifi and mobile networks to connect to devices. Make sure your Wifi adaptors are turned on in every device to start receiving instructions
- Have you used labels? Using custom and template labels on your devices may help you group them up in the future. In fact, our newest feature lets you create groups with their own permissions
- Have you tested your setup? Try some basic commands on devices you have at hand. Actions like triggering a message or alarm on the device will work to make sure the connection between your Panel and the device is a-ok
- Did you make sure your connections are secure? Prey collects a lot of information about your devices, so it’s essential to protect your —and your client’s— privacy. Make sure you activate MFA to access your Panel, and ensure you have strong passwords for every login in the chain
- If something doesn’t look right, please visit our Help Center or contact our Support team
Using Control Zones to monitor reactively
One of the most useful tools in your Prey arsenal is Control Zones. Harnessing the power of geofencing to control and monitor can help you automate security tasks, to let the machine be the guardian! Using Prey’s Control Zones, you can trigger actions when a device enters or leaves a radius you determine on a map.
To start using Control Zones, click on the Control Zones button on the left menu. By dragging the pin or selecting an address on the map, you can easily create a geofence with the radius you need. One of the most common geofences is the streets around the office, to have complete control when a device exits or enters it.
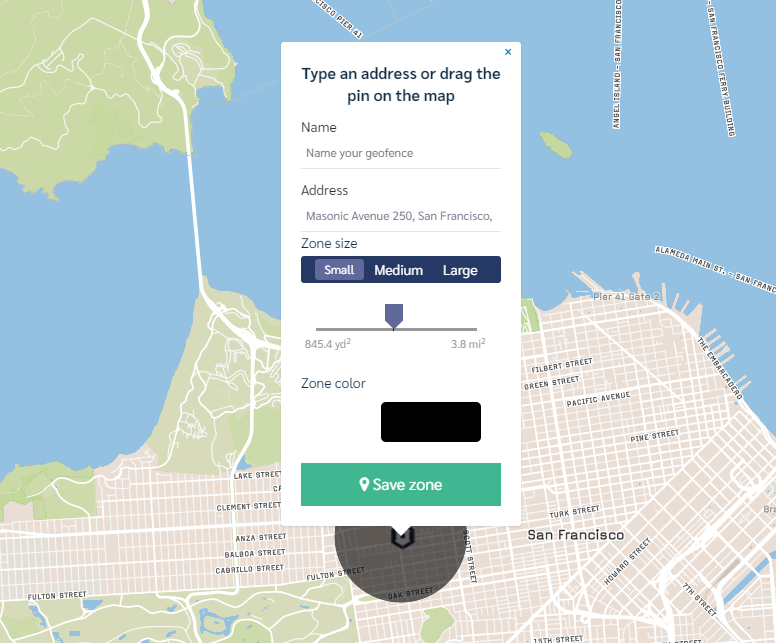
After creating a zone, you may add an action to trigger when a device enters or exits the Control Zone. Besides alerting you with an email —which is useful if you’re trying to have complete control— you can execute several actions: sound an alarm, send an alert message to the person moving the device, lock the screen, or mark the device as missing, one of our main anti theft features.
.png)
Control Zones can be set all around the world. Here are some ideas to improve your monitoring:
- If you’re lending devices at a school, set a Control Zone around the perimeter and add a Screen Lock action when the device exits it, to avoid improper usage by students
- If you have strict policies on your organization’s premises —such as “no device exits the building”— set a Control Zone on the block around the office with an email alert and a Mark As Missing action, to alert you immediately
Using Automations to trigger reactive solutions
Automations in Prey work as scheduled actions based on reactive events: you decide what behavior triggers the automation, and what happens. A lot of our users use Automations based on time. For example, setting a curfew to block devices over a certain period of time —schools on weekends, for example— to streamline a process that can be tiresome. But how can we use Automations for tracking purposes?
Two events can help you reactively to protect and make sure your device doesn’t fall in the wrong hands:
• Hardware changes: Triggers a response when Prey detects a change of hardware in a device, such as any hardware component changes that occur since the last connection with Prey (Motherboard & BIOS, CPU, RAM, or Network Interfaces).
• Device not connected to Prey: Triggers an action when a defined number of days have passed with the device not checking in to the Prey servers.
These two automations are hugely beneficial when you are dealing with large fleets or important remote devices. You can automatically lock a device if any piece of hardware is changed, or mark it as missing if it doesn’t connect to our servers without any effort.
To start using this helpful tool, click on the Automations button on the left menu of your Prey Panel. Automations only need a name, a trigger, and an event. Then, you need to select devices that will be affected by this, and done!
.png)
Using Location History to monitor devices on a time frame
A very helpful tool to consider adding to your arsenal is Location History. This tool can help you visualize past locations of devices and follow the activity of phones and laptops closely throughout the day. This is especially useful when analyzing patterns of movement of your fleet and detecting anomalies in their schedule, such as an employee taking a laptop home when they shouldn’t.
Location History is also a great source of information for compliance reasons: you can easily export a CSV with the location information of a device for up to a month.
To start, look for the button “Show previous locations” on the map when you have a device selected.
.png)
By choosing a date on the upper menu you can locate the device instantly, and where it was that specific day.
.png)
Using Reports when disaster strikes
We all hate when a device goes missing. And it can get worse when a malicious actor steals it. Personal photos and documents are one thing, but when a device with payroll data or confidential information falls into the wrong hands, things can turn sour very quickly. To maximize the possibilities of finding that device, Prey has missing reports that can document the status of the device while you found it.
By marking your device as “missing”, a window in our Panel will let you configure your reports. You may choose to take pictures using the device’s cameras or take screenshots to get a grasp of the activity on your device while its captor uses it.
.png)
Shortly after, you will start receiving reports that you can check directly on the “Missing reports” tab on that device.
.png)

