Most organizations either brush off dark web threats as someone else’s problem or get flooded with so many alerts they end up tuning them out. The issue isn’t a lack of data, it’s too much of the wrong kind, scattered across forums, dumps, and chat channels. Without structure, what could be a warning sign becomes background noise, leaving your organization exposed to everything from data breaches that make headlines to hidden threats such as covert identity theft or credential theft, as well as the loss of sensitive data and other sensitive data such as intellectual property, proprietary information, and internal organizational data, to the slow bleed of compromised accounts that derail operations and attract regulatory scrutiny. Monitoring for potential data breaches is crucial to prevent unauthorized access and security incidents.
That’s where a threat intelligence lifecycle makes the difference. Instead of reacting to whatever pops up, this approach helps you define what matters, collect only what’s useful, and turn it into insight your team can act on. It’s how you go from chasing leaks to staying ahead of them.
Understanding the Dark Web
Think of the dark web as the internet's hidden neighborhood – one that sits just beyond the reach of your everyday Google searches. While the surface web welcomes everyone with open arms, this shadowy corner requires special tools like Tor to even find the front door. Here's where things get concerning for your business: this anonymity creates the perfect environment for cyber threats to flourish. Bad actors gather in these hidden spaces to trade your stolen data, share malicious software, and cook up their next schemes. But here's the empowering part – when your security team understands how these underground markets operate, you're no longer flying blind. By getting familiar with how sensitive information flows through these hidden channels, you can anticipate threats and build stronger defenses. It's about staying one step ahead in a game where knowledge truly becomes your competitive advantage.
Dark Web Sites and markets
Think of dark web markets as the hidden underground bazaars of the internet—places where cybercriminals gather to buy and sell stolen information, harmful software, and other digital contraband that can seriously impact your business. These shadowy marketplaces attract people who want to profit from your most sensitive data, whether that's customer credit card details, employee login information, or your company's valuable intellectual property. What makes these threats particularly challenging is how quickly they evolve and adapt—new ransomware services pop up regularly, fresh batches of stolen data appear without warning, and attack methods constantly shift and improve. Here's why this matters for your organization: keeping tabs on these dark web activities isn't just a nice-to-have security measure, it's essential for protecting what you've worked hard to build. When your security team monitors these underground spaces, they can actually spot potential attacks before they happen and take protective steps before your sensitive information gets exploited by bad actors.
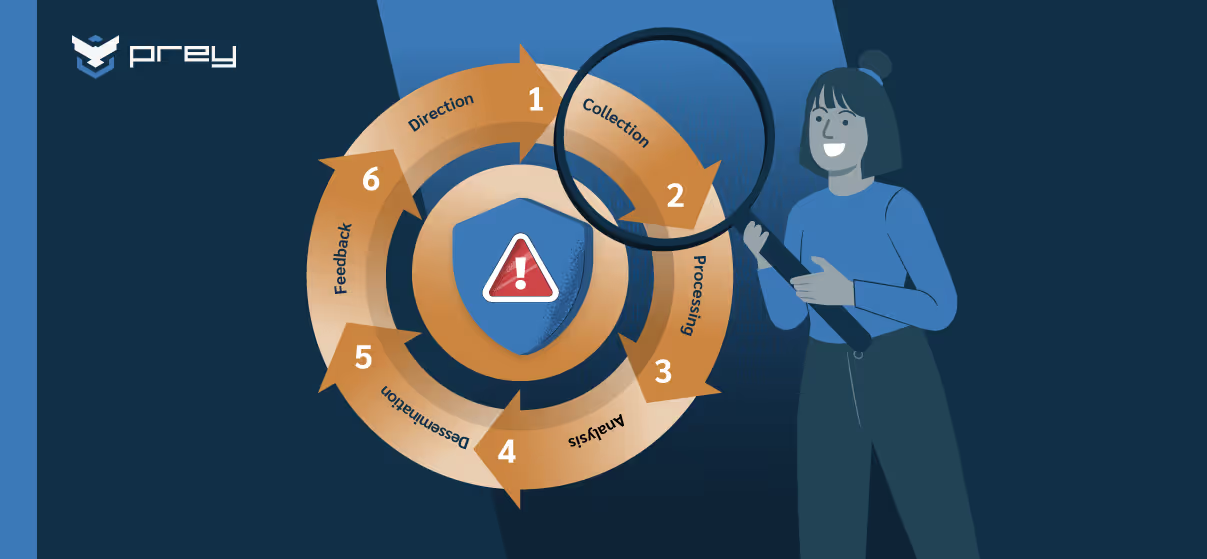
What is the threat intelligence lifecycle?
The threat intelligence lifecycle might sound like something reserved for massive security teams with infinite resources, but it’s actually a clear, step-by-step way to make sense of chaotic signals, especially from the dark web and other threat sources such as breach dumps, forums, and online channels. It’s not a complicated framework, and it doesn’t have to slow you down.
In fact, it brings much-needed structure to an otherwise reactive process, transforming your security stance from perpetual firefighter to proactive guardian. Most importantly, this isn’t a one-time setup. Threats evolve, new leaks surface, and your priorities shift. That’s why this approach loops continuously, helping you stay aligned and ready. By ensuring you collect only what’s useful, the data collected from these threat sources becomes critical for effective analysis and timely response.
Direction
This first step is all about setting your sights. Before you even look at data, you need to know what matters to your organization. Are you tracking leaked credentials of your executives or the whole company? Flagging vendor domains? Direction gives focus, helping you filter noise before it even starts. Think of it as aligning your radar with actual business risks and those ever-present compliance mandates like HIPAA or GDPR, and ensuring your service aims clearly define the focus and objectives of your dark web monitoring efforts.
Collection
Once you know what to look for, it’s time to gather the intel using advanced tools designed to access deeper layers of the dark web. That means pulling data from a mix of sources—breach dumps, dark web forums, marketplaces, even botnet logs. It can be manual or automated, leveraging a specialized search engine for the dark web to enhance the collection process, but the goal is the same: grab everything relevant before it disappears or gets buried.
Processing
Raw data is messy. This raw intelligence, gathered from various dark web sources, requires processing before it becomes actionable. At this stage, you’re cleaning it up, validating what’s real, and enriching it with context. Is the credential still active? How recent is the leak? Was it tied to an administrator account? This step helps turn scattered bits of data into something you can actually use.
Analysis
Now that the data is cleaned and verified, analysis turns it into something meaningful. This is where patterns emerge, risks are assessed, and context is added. Is this leak linked to other incidents? Does it hint at a larger campaign? And critically, how does this impact our risk register or upcoming compliance audit? Insight—not just information—starts to take shape here. This analysis delivers actionable insights and crucial insights that inform strategic security decisions.
Dissemination
Insights are only useful if they reach the right people, as timely dissemination supports faster incident response and minimizes potential damage. This step ensures that security teams, IT ops, identity managers, and even legal or compliance teams get the intel they need in time to act. It’s also about having the right info, in the right format, if you need to brief senior management or the board on an emerging threat. It’s about turning knowledge into decisions, without letting it get lost in a silo.
Feedback
No cycle is complete without a loop back. After action is taken (or not), feedback helps evaluate what worked, what didn’t, and where you need to adjust. Maybe you missed something important, or maybe you flagged too much. Either way, this step keeps the cycle sharp and relevant. Feedback may also highlight the need for further investigation into missed threats or suspicious incidents.
Dark Web intelligence unique challenges
The dark web brings its own quirks to the threat intelligence lifecycle. Unlike traditional data sources, it’s unpredictable, fragmented, and constantly shifting. The deep and dark web contains many hidden corners and hidden web areas, including hidden websites that are unindexed, used for illicit activities, and require specialized tools or browsers to access and monitor. Tools that work today might miss the mark tomorrow. These unique challenges can trip up even experienced teams—but with the right mindset and process, they become manageable and, in some cases, even advantageous.
Volatility of data sources
Dark web sources are unstable by nature, with criminal forums especially prone to sudden disappearance or rebranding. Forums disappear overnight, vendors change names, and Telegram channels pop up faster than you can track them. The trick is to rely on adaptable tools that can pivot with these shifts and maintain broad coverage without clinging to any one source too tightly.
Volume vs. Relevance
It’s easy to drown in leak data. Not everything dumped online is worth your time, and most of it isn’t; prioritize exposed data that poses a real risk to your organization. Solving this means applying filters: target only key assets, apply risk scoring, and focus on credentials with direct ties to your environment. Precision matters more than quantity, saving your team from chasing ghosts and battling alert fatigue.
Ties to other threat actors
A single leak might be part of something bigger, as malicious actors often collaborate or intersect across different dark web activities. Initial access brokers, ransomware groups, and phishing kits often intersect in subtle ways. Identifying these connections takes correlation and contextual enrichment. It’s not just about what was leaked, but who might be involved and what comes next.
Risks of false positives or delayed alerts
Not every leaked credential is real, and even real ones might hit your radar too late. To cut through the fog, it helps to validate leaks quickly and prioritize based on risk. Build in alerting thresholds and double-check against live systems so you’re not chasing ghosts—or missing threats entirely. Incorporating mechanisms for early warnings enables security teams to respond to threats before they escalate.
The Importance of Dark Web Monitoring Tools
Here's the truth about dark web monitoring tools—they're not just another security add-on, they're your early warning system in today's digital landscape. Think of these smart solutions as your digital scouts, constantly scanning the shadowy corners of the internet where stolen data gets traded like trading cards. When your sensitive information—whether that's customer details, financial records, or those confidential files you'd rather keep private—shows up where it shouldn't, these tools spot it fast and send you real-time alerts that actually matter. This isn't about playing defense after the damage is done; it's about getting ahead of the game. When your security team gets actionable intelligence the moment threats surface, they can jump into action quickly, dramatically cutting down the chances of a devastating data breach. Companies using these tools aren't just protecting data—they're gaining genuine insights into what threats are actually out there, staying one step ahead of the bad guys, and making sure their most valuable information stays exactly where it belongs: safely in their hands.
How to operationalize the lifecycle in your org
Putting the threat intelligence lifecycle into motion won’t look exactly the same for every organization. Different industries, sizes, and risk profiles will shape how it all plays out. Still, the most effective setups tend to follow similar patterns—ones that center around clarity, automation, and action. Integrating dark web threat intelligence into your entire security stack ensures comprehensive protection across all layers of your cybersecurity measures. It’s less about copying a playbook and more about building a rhythm that fits your team and priorities.
Aligning threat direction with business risk
Start by mapping your intelligence goals to what actually matters to the business. Finance departments might be high-value phishing targets and need to adhere to PCI DSS. HR teams handle sensitive personal data governed by regulations like GDPR. Executives are common social engineering bait. Aligning efforts this way helps ensure you’re not just collecting noise, but watching the right signals that could impact your compliance posture or bottom line, while also strengthening network security by focusing on the most relevant risks.
Risk-based processing: prioritize credentials with admin access
Not all leaked credentials carry the same weight, especially when it comes to compromised credentials with elevated privileges, which pose a heightened risk. Processing with risk in mind lets you act faster on the threats that matter most. A compromised admin account or service login should always take priority over a general user. Rank what’s surfaced and move the needle where it counts.
Cross-functional dissemination
Once insights are ready, they need to reach the right people, not just the SOC. IT admins may need to act on exposed credentials, while Legal or Compliance might need to log the incident. A smooth handoff across teams ensures faster, smarter decisions without information getting stuck in silos.
Documenting for due diligence and compliance
Building this structured approach, with clear documentation at each step, isn’t just good practice; it’s gold during an audit. It demonstrates due diligence and a mature security program to auditors and stakeholders alike, showing you’re not just reacting, but actively managing cyber risk—while also providing evidence of compliance to government agencies and regulators.
Continuous improvement loop: false positive feedback, new asset tagging
The lifecycle doesn’t stop at action. It learns. Feeding back results, like false positives or missed detections, helps refine detection rules and update asset inventories. Maybe a new executive wasn’t being monitored, or an outdated email slipped through. Adjustments like these keep your threat intel process sharp and current. Continuous feedback can also help identify and mitigate insider threats that may otherwise go undetected.
Anatomy of a leak response: Start to finish
Even if you’ve got the lifecycle mapped out and the tools in place, it helps to see how it all plays out in real time. A concrete example brings the process into focus and shows how each step connects to the next. Let’s walk through a fictional scenario that mirrors what many security teams face on any given week.
The risk tied to potential data exposure is deemed high. There is also a significant risk to private information, as exposed credentials could be misused for identity theft if not addressed quickly.
The team immediately initiates a response, focusing on containing the threat and protecting sensitive company data no matter where the endpoint is. This response helps prevent a data breach and limits the impact of data leaks or other attacks that could follow.

Scenario:
An email and password tied to your company domain shows up on a well-known credential stuffing forum. The password isn't hashed, and the combo appears to be fresh. What happens next?
- Detection via DWM: Your dark web monitoring system picks up the leaked credentials and flags them based on a match with your domain. This triggers an internal alert for review by the security team.
- Correlation with internal directory: The team cross-references the leaked email with your user directory. It turns out the account is still active, and the password matches what was previously used in a third-party tool. This raises suspicion of password reuse.
- Alert escalated based on access level: Since the email belongs to a user with elevated privileges in the ERP platform, the incident is escalated for immediate action. The risk tied to potential data exposure is deemed high.
- Trigger remediation controls: The account is forcefully logged out, a password reset is enforced, and the user is contacted. Since the user's laptop hasn't checked in recently, and with a hybrid workforce, you can trigger a remote wipe command is queued in case the device is compromised or confirmed lost/stolen, protecting sensitive company data no matter where the endpoint is.
- Add insight to IR report and adjust monitoring direction: The incident is documented, and the post-mortem reveals that third-party tools used by client-facing teams aren't properly monitored. The security team tags these tools as new monitoring targets and tightens password policies across departments.
Tools that help
Not every organization has a full threat intel team at the ready, and that’s okay. When it comes to the "Collection" and "Processing" phases of the dark web threat intelligence lifecycle, specialized dark web monitoring tools are your frontline. These are the solutions designed to continuously (and often anonymously) scan forums, marketplaces, paste sites, and illicit channels where compromised data and threat actor discussions occur. They're built to find mentions of your domains, executive names, IP addresses, or leaked credentials before they turn into major incidents.
While these dedicated dark web monitoring services provide the raw intelligence, many IT teams then feed these alerts into their broader security ecosystem. For instance, insights from a dark web monitoring tool can be integrated with SIEM solutions (like Splunk, LogRhythm, Microsoft Sentinel, or IBM QRadar). This allows your security operations to correlate dark web findings with internal network activity, endpoint alerts, and other security logs, giving you a more holistic view of potential threats and helping to prioritize responses. The DWM tool finds the needle; the SIEM can help you see where that needle might prick.
One option to consider is Prey Breach Monitoring. It’s built to support several stages of the lifecycle, especially detection and processing For mid-sized security teams or IT departments without a dedicated threat intelligence analyst, Prey fills the gap with automation and contextual alerts. It helps surface what matters, skips the fluff, and gives you a head start on fast-moving threats, while also protecting your devices.
What to look for in a lifecycle-supporting tool:
- Real-time leak detection
You want alerts as close to the breach as possible. Look for tools that continuously monitor dark web sources and alert you the moment your domains or credentials appear.
- Risk scoring / contextual enrichment
Raw leaks are just the beginning. Good tools provide context—was the password reused? Is this account privileged? Risk scoring helps you prioritize instead of guessing.
- Integration with SIEM or IAM
Threat intel should feed into your existing security infrastructure. Look for tools that plug into your SIEM or identity systems to streamline handoffs and automate action.
- Scalable alerting
Whether you’re a five-person team or handling hundreds of endpoints, the tool should let you tune alerts by priority, asset type, or team role so you don’t drown in noise.
- Actionability for remote assets
The ability to not just detect a credential leak, but to tie it to specific devices—especially remote ones—and initiate security actions (lock, wipe, locate) directly from the platform. This closes the loop from detection to remediation, which is a huge win for busy IT teams.
- Clear reporting for compliance and management
Look for tools that can generate straightforward reports on detected threats and actions taken. This makes briefing stakeholders and satisfying auditors much less painful.
Make Dark Web intel work for you
Threat intelligence without action is just trivia—interesting, maybe, but not helpful. What makes it valuable is structure. A lifecycle approach turns scattered signals into clear next steps, helping your team shift from reacting after the fact to staying ahead of the threat. It’s how dark web intel becomes a real defense asset, giving you and your team a bit more breathing room and the confidence that you’re actively reducing organizational risk.
Check your dark web exposure now.