Losing a laptop is stressful — but for IT and security teams, it’s more than just lost hardware. A single stolen laptop can expose confidential files, patient records, or financial data, and even trigger compliance violations. Knowing how to track a stolen laptop quickly and securely is critical to minimizing risk.
In this guide, we’ll walk through practical steps IT managers, admins, and business leaders can take to locate stolen laptops, protect sensitive information, and strengthen policies for future incidents.
How to track and recover a stolen laptop (step-by-step)
The most reliable way to track a stolen laptop is with dedicated tracking software. While consumer tools like Windows “Find My Device” or Apple “Find My Mac” can help in individual cases, IT teams managing hundreds of laptops need enterprise-grade solutions. Prey’s tracking panel allows you to locate, monitor, and take action across your entire device fleet.
The most reliable way to track a stolen laptop is by using dedicated tracking software. Built-in options like Windows Find My Device and Apple’s Find My Mac can help in individual cases, but organizations managing hundreds or thousands of endpoints need more powerful tools. Prey’s enterprise platform allows IT teams to see where laptops are in real time, monitor suspicious activity, and protect sensitive data with security actions like remote lock and remote wipe.
Here’s a detailed roadmap you can follow to maximize your chances of recovering the device and protecting your information:
Step 1: Make Sure Tracking Is Enabled Before a Loss Happens
Tracking is only effective if it’s activated before the laptop goes missing. For businesses, this means making device enrollment part of your IT onboarding process.
- With Prey: Add every company laptop to your Prey dashboard during setup. Confirm tracking is active and security actions (lock, wipe, kill switch) are configured.
- With Windows/macOS: Make sure “Find My Device” (Windows) or “Find My Mac” (macOS) is turned on during the initial setup.
Tip for IT teams: Run regular audits to verify all devices in your fleet are enrolled and properly configured.
Step 2: Log into your tracking dashboard immediately
Time is critical when a laptop goes missing. As soon as the incident is reported:
- With Prey: Log into the Prey Control Panel, select the missing laptop, and mark it as “Missing.” This activates location tracking and evidence collection.
- With OS tools: Sign in to your Microsoft account (for Windows) or iCloud account (for Mac) to view the device’s last known location.
Why this matters for IT: Prey’s centralized dashboard means admins don’t need individual user credentials — one login provides visibility over the entire fleet.
Step 3: Monitor device signals
Tracking isn’t just about a GPS pin on a map. Advanced software collects multiple signals that can help pinpoint the laptop and identify who is using it:
- Location history: Shows where the laptop has traveled since being marked missing.
- Wi-Fi networks: Reveals which networks the device has connected to.
- Screenshots and camera captures: Provide evidence of the user currently operating the laptop.
Compliance angle: These reports create a verifiable trail that supports law enforcement and regulatory audits (HIPAA, GDPR, PCI DSS, etc.).
Step 4: Take remote security actions
Sometimes recovery isn’t immediate, or the laptop is in an unsafe location. In these cases, the priority shifts from retrieving the device to securing its data.
- Lock the device: Prevents unauthorized access to files or applications.
- Display messages/alerts: Send a notification to the laptop with instructions to return it (e.g., “This is a company device. Please return to IT.”).
- Remote wipe: Erase sensitive files, financial information, or patient records if there’s a risk of breach.
- Kill Switch: Disable the machine entirely by destroying the Master Boot Record, making it unusable until IT restores it.
For IT teams: These options ensure you remain compliant and reduce liability, even if the laptop never comes back.
Step 5: Report and document the incident
If you’ve located the device, especially in a risky area, involve law enforcement instead of retrieving it yourself. Provide them with the recovery reports from Prey, which include timestamps, location data, and photographic evidence.
At the same time:
- Document the incident internally for your IT/security records.
- Notify compliance officers if sensitive data was at risk.
- Update the employee or department involved, ensuring next steps are clear.
Step 6: Review and improve your security policies
After any laptop theft or loss, use the experience to strengthen your organization’s device security.
- Reassess your onboarding checklist to ensure tracking is always enabled.
- Tighten remote access policies (VPNs, MFA, conditional access).
- Expand fleet monitoring with geofencing alerts.
- Conduct employee training on reporting incidents quickly.
Tracking a stolen laptop isn’t just about getting the hardware back. For IT and security leaders, it’s about protecting sensitive data, maintaining compliance, and proving control over company assets. Dedicated solutions like Prey provide the visibility, evidence, and security actions that consumer tools simply can’t match.
How to recover a stolen laptop using Windows 10 or higher
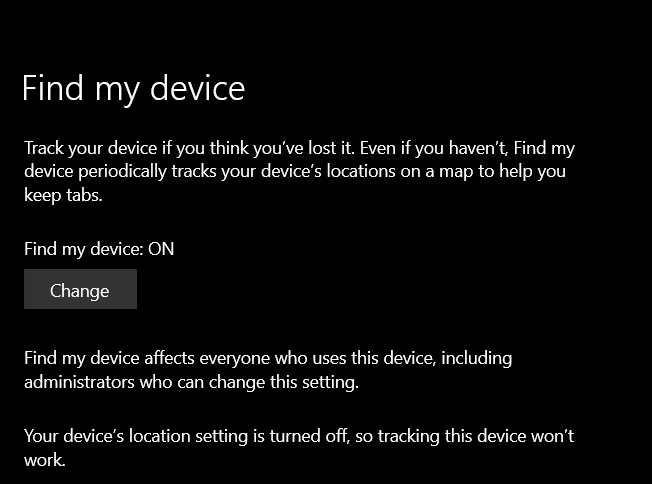
If you want to track a laptop running Windows 10 or higher, you can use the pre-installed "Find My Device" software to recover your laptop. Of course, you must have this service activated to use it to locate your device.
If you already have it activated:
- Go to Microsoft's device management page.
- Select the device you want to find.
- Click on "Find my device".
- You're done!

If you want to activate it:
- Press the "Start" key or press the key combination CTRL+S.
- Search for "Find My Device".
- Turn this option on.
- Try this option by performing the steps listed above.
How to recover a stolen Mac laptop
To track a stolen Mac laptop you must follow similar steps to those for Windows computers. Apple devices come with a factory-installed application for tracking devices. Of course, you must also have activated it beforehand.
If you have already activated it:
- Launch the Find My app on another Apple device, then select the Devices tab.
- On the Internet, log in to iCloud.com/find, then click "All Devices".
- Select the MAC device you need to find to view it.

If you want to activate it:
- On your Mac laptop, open the Apple menu, then "System Settings" and click your profile at the top of the sidebar. If you don't see your name, click Sign in with your Apple ID to enter your Apple ID or to create one.
- Click "iCloud" on the right.
- Click "Find My Mac", click Enable and click "Allow" when asked if you want "Find My Mac" to use your Mac's location.
- Test your settings by following the steps above

How to track and recover a stolen laptop using Prey
Through the Prey app, you can track Apple devices such as laptops and mobiles, Windows devices, and Android mobile phones. Please note that, as with the previous apps, you need to install the app and add your devices beforehand to be able to track an associated laptop.
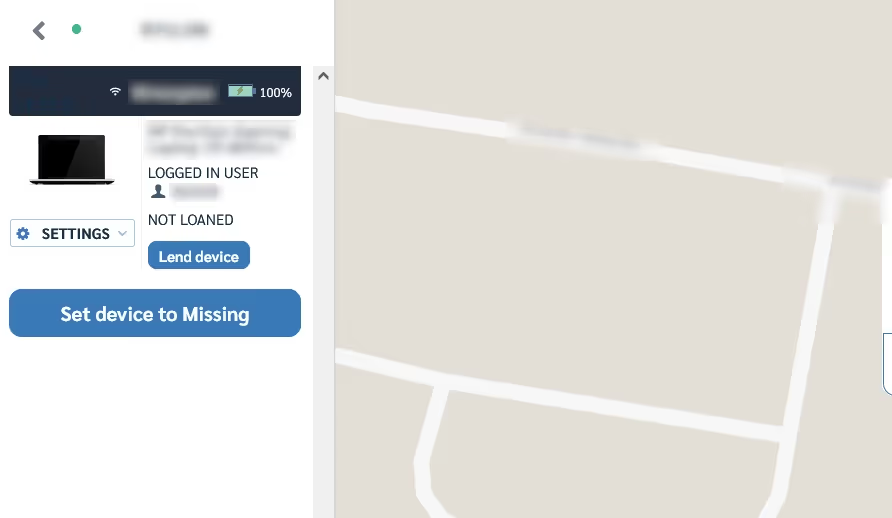
If you already have Prey installed:
- Log in to the Prey Panel.
- Select the "Devices" tab in the right-hand menu
- Select the device to track.
- Mark as Missing and go to the missing reports tab
- Follow the device’s steps through the location history data
If you want to activate it:
- Create a Prey account
- Install the application on the device you will be using it on.
- Once installed, add the device to the dashboard
- Verify the correct configuration of the device by following the steps in the list above.
Additional actions you can do with Prey tracking capabilities
Track compatible Android, iOS, MacOS, and Windows devices
You can track multiple devices using our software, this way, you can locate and generate reports for fleet management. This is very useful for IT departments that want to keep track of fleets composed of laptops and smartphones with sensitive information and locate borrowed devices.
Keep an eye on the location history of devices
Prey can generate location history reports, so employers and IT departments can keep an eye on where certain devices have been. This can help in recovery cases, as said information can be used to create a list of possible places where a device can be found.
Activate automatic actions such as alerts and messages for specific geographic areas
Our software can be used to create a geofence zone, which can be used to designate safe or unsafe location zones. This in turn can be used to alert device owners about taking their devices out of a safe zone and message them to return the device or take extra precautions with it.
Disable the device with a Kill-Switch or delete its data with a remote wipe
You can use our kill-switch feature to remotely disable a stolen laptop that cannot be recovered. You can also use Prey to delete sensitive information stored in a device, which can be used to remove confidential information for a lost laptop or to wipe the data of a previous employee to lend the device to a new one.
Create reports including photos, screenshots, and device location data
Prey can generate customized reports that can help in recovery scenarios. Said reports include pictures taken from the lost laptop’s camera, screenshots of the device while it’s being used, location history, Wi-Fi data, and even changes done to the device’s hardware. These reports are very useful, as they can be used to identify who is using the device, where it is, and what it's being used for.
What to do after tracking your stolen laptop
Now that you've found your computer, you need to ask yourself the question: "Can I get it back without help? If you have located your laptop in a safe place, such as your work office or a hotel, you can probably go and get it without any problems.
But if it turns out that your laptop is in an unknown or potentially dangerous area, chances are that someone has taken it. In this case, the best thing to do would be to ask the local authorities for help, just make sure you have all the relevant information and witnesses who can identify your laptop as yours and help them recognize it.
As we already said, the reports that our software generates are very useful for these kinds of scenarios, as they can help the local authorities identify the person that took your laptop and verify that you’re the real owner of the device.
What to do if you can't recover your stolen laptop
If you can't recover your device, you can still take action to protect the data you have on it. The first thing you should do is use the same software we mentioned above to lock it down.
Protect your information
If you can’t recover your laptop, you can still protect your information. Even if you don’t have physical access to its files, you can take some actions to reduce the potential damage that you can suffer from losing your device.
Recover your important data
If your laptop has access to software that allows you to back up your files to the cloud, then you should start uploading any important files to your cloud storage as soon as you lose them. The following steps involve deleting most of your files and information from your lost laptop, so you might want to quickly save your data before erasing it.
Delete your lost files
The next thing you should do is wipe your lost data. While Microsoft’s Find My Device doesn’t allow you to delete files, you can use Prey to remotely delete your files on windows devices. Macs are also compatible with our software, and you can also use Apple's Find my Mac to remotely erase your files.
Change your passwords and close your active sessions
Closing your active sessions to online services and platforms is the second thing you should do as soon as you lose your laptop. Doing this will prevent whoever has it from accessing critical services, such as your social media accounts, emails, or your bank accounts. You can do this by logging in from another device, such as your mobile phone, to close active sessions on other devices.
You should also change all of your passwords, this usually closes any active sessions of most online services and platforms, but even if it does you should still close your other active sessions. Some web browsers, like Firefox, allow you to wipe sync data like your saved passwords, which is something that you should do.
Notify your banking services
If you had your cards saved in your preferred e-commerce sites or their data stored in a document on your lost laptop, then you should notify your bank. This way you can save yourself from suffering additional financial losses from unauthorized purchases.
Remotely kill your laptop
You can use Prey’s Kill-Switch to remotely kill your device. This feature works by destroying the Master Boot Record of your computer, rendering it unusable. You can use this to get the last laugh, even if you didn’t recover your laptop.
Keep in mind that our Kill-Switch doesn’t permanently destroy the laptop, as any IT tech can apply some software magic to restore the device to its factory settings. This makes the kill-switch feature a very useful tool for IT teams that want to close unauthorized access to unruly employees, recover the device, and then restore it to make it work again.
Why IT & security teams need enterprise tracking
For IT and security teams, recovering a stolen laptop isn’t just about getting the hardware back. The real concern is the sensitive information stored inside — patient health records, financial data, intellectual property, or employee details. If a laptop goes missing, it can quickly escalate into a compliance violation, reputational damage, and even financial loss.
Compliance and legal requirements
Organizations are held to strict data protection laws worldwide. Regulations like HIPAA in healthcare, GDPR in the EU, or Chile’s Cybersecurity Framework Law (Law 21.663) require businesses to demonstrate that lost or stolen devices are controlled, monitored, and — if necessary — securely wiped. Without proof of control, companies risk audits, fines, and lawsuits.
Enterprise tracking tools like Prey generate detailed audit logs and recovery reports with timestamps, locations, screenshots, and even camera captures. These reports serve as a chain of custody, helping businesses prove to regulators and auditors that they acted quickly and responsibly.
Managing device fleets at scale
Consumer tools like Find My Mac or Find My Device work fine for individuals, but IT departments often manage hundreds or thousands of laptops across multiple operating systems. This scale requires more than one-off tracking:
- Centralized dashboard: Monitor all devices from a single pane of glass.
- Multi-OS support: Windows, macOS, Linux, Android, and iOS.
- Location history: Track device movement over time, not just a single location ping.
- Geofencing alerts: Get notified when a laptop leaves a secure zone (e.g., office, campus, hospital).
With these tools, IT leaders can identify patterns, investigate suspicious activity, and make better decisions about incident response.
Insider threats and employee offboarding
Not every “stolen” laptop involves an outside thief. Insider threats — such as disgruntled employees, contractors, or even honest mistakes during offboarding — are just as common.
Enterprise tracking software gives IT control over these situations by:
- Locking or disabling laptops when an employee refuses to return equipment.
- Remotely wiping sensitive files to prevent data leaks.
- Generating recovery reports that provide evidence in HR or legal disputes.
This level of control reduces organizational risk and prevents sensitive information from walking out the door.
The bottom line
Enterprise tracking isn’t just about recovering a device — it’s about protecting data, maintaining compliance, and proving accountability. Without it, IT teams are left with blind spots that can cost the business far more than the price of the laptop.
Prey bridges this gap by offering fleet-level visibility, compliance-ready reports, and advanced security actions that consumer tools simply don’t provide.
Frequently asked questions
How can I locate a lost or stolen laptop without tracking software?
One way to try and locate a lost or stolen device is by offering a reward for its return, as this could provide some incentive for someone who may have found it. Additionally, you can advertise the fact that your laptop has gone missing on social media and/or print posters and leaflets about it to spread awareness around your local area.
What measures should I take if my laptop gets lost or stolen?
It’s important to take extra precautionary measures to protect any personal data that may be stored on the device. This includes changing all passwords associated with the computer, securing other devices connected to the same network, contacting banks and credit card companies linked to the device, enabling two-factor authentication for online accounts associated with it, and deleting sensitive information from cloud storage services.
What happens if someone finds my laptop and I can’t locate it?
Depending on how they find it, they may offer to return it out of kindness. However there are no guarantees that this will happen. Offering a reward might increase their chances of being found.




