Most organizations today have the basics covered—firewalls are in place, antivirus software is running, and maybe even multi-factor authentication is set up. And that’s great. But the reality is, modern threats don’t always trip the alarms we expect. Attackers today don’t always break in with brute force—they slip through unnoticed, using tactics that mimic normal activity. To truly protect systems, security teams need to understand how attackers operate, not just block the obvious stuff.
That’s where MITRE ATT&CK makes a difference. It’s a knowledge base built on real-world attack behavior, showing exactly how threat actors carry out their missions. Instead of just flagging threats at the finish line, it helps you see the steps they take along the way. With ATT&CK, security teams get a clearer view of the methods behind the breaches.
What is the MITRE ATT&CK framework?
MITRE ATT&CK, short for Adversarial Tactics, Techniques, and Common Knowledge, is a framework created to map out how attackers behave once they’ve made it into a system. Developed by MITRE, a U.S.-based nonprofit that supports government and private sector cybersecurity efforts, ATT&CK started as a research project and quickly evolved into a widely adopted reference for understanding threat behavior in the real world.
The framework is organized into matrices that group tactics and techniques. Many techniques are broken down further into sub-techniques, adding more depth and precision.
The MITRE ATT&CK Matrix
The MITRE ATT&CK framework consists of multiple matrices, each tailored to a specific domain, including Enterprise systems like Windows, Linux, and macOS; Mobile platforms such as Android and iOS; and even Industrial Control Systems (ICS), which are crucial for infrastructure operations.
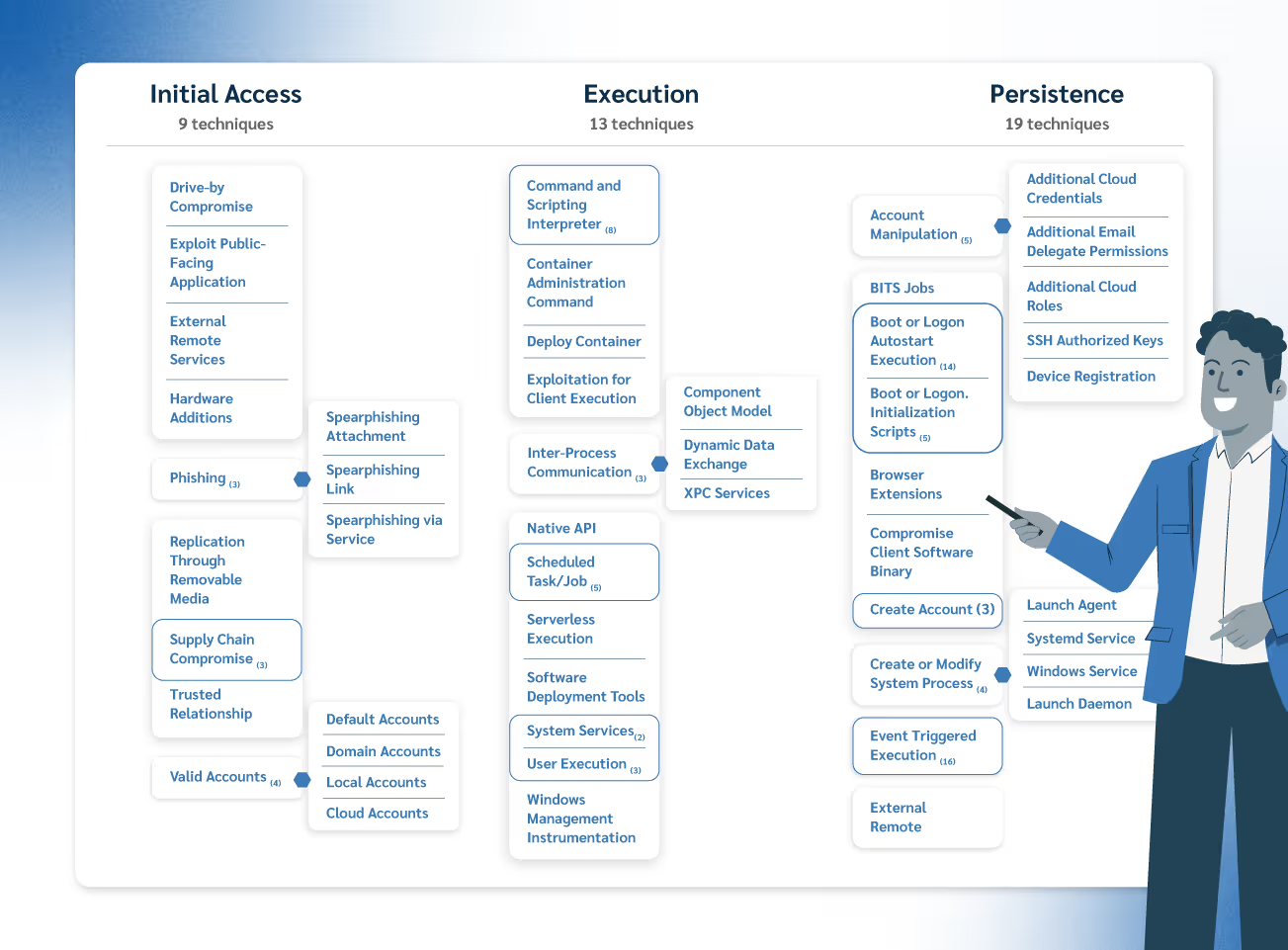
Enterprise Matrix
The Enterprise matrix is the most comprehensive of the three and covers a wide range of systems found in corporate environments. It’s designed to help security teams track attacker behavior across everything from local machines to cloud platforms.
Within Enterprise, ATT&CK breaks down even further into the following sub-matrices:
- Windows: Techniques specific to Microsoft environments, often targeted due to their wide usage.
- macOS: Covers how attackers target Apple computers, including unique persistence and execution methods.
- Linux: Tracks techniques used against Linux servers and endpoints, popular in enterprise and web infrastructure.
- Cloud: Includes attacks against Microsoft 365, Google Workspace, Azure AD, and both SaaS and IaaS environments.
- Network: Focuses on how attackers exploit network infrastructure, including routers, firewalls, and protocol misuse.
Mobile Matrix
The Mobile matrix focuses on the techniques adversaries use against smartphones and tablets, specifically Android and iOS. It includes actions like exploiting mobile apps, abusing permissions, and accessing sensitive data through insecure configurations. With mobile devices now a standard part of business operations, this matrix helps ensure they aren’t overlooked in your defense strategy.
Within the Mobile matrix, ATT&CK breaks techniques down by operating system:
- Android Submatrix:
- Includes methods like exploiting malicious apps, bypassing app sandboxing, abusing Android-specific APIs, and using legitimate services for unauthorized actions.
- iOS Submatrix:
- Focuses on techniques such as jailbreaking, leveraging enterprise provisioning profiles, targeting iCloud location features, and manipulating mobile device management (MDM) configurations.
ICS Matrix
The ICS matrix addresses threats to Industrial Control Systems, which are used in sectors like energy, water, and manufacturing. Attacks here can have real-world consequences—think power outages or production shutdowns. This matrix reflects the specific techniques used to disrupt, manipulate, or take control of critical infrastructure systems, and is essential for protecting national and industrial assets.
Key MITRE ATT&CK components concepts
MITRE ATT&CK systematically organizes how attackers behave in real-world scenarios, categorizing their actions to help defenders clearly recognize patterns and respond effectively. Rather than focusing only on outcomes or specific threats, ATT&CK provides a structured way to break down adversary behavior into distinct categories—each detailing different aspects of how attackers plan and execute cyber operations.
Tactics
Tactics describe the strategic goals of an attacker—the "why" behind their actions. These represent broad objectives such as gaining initial access, moving laterally across networks, or stealing data.
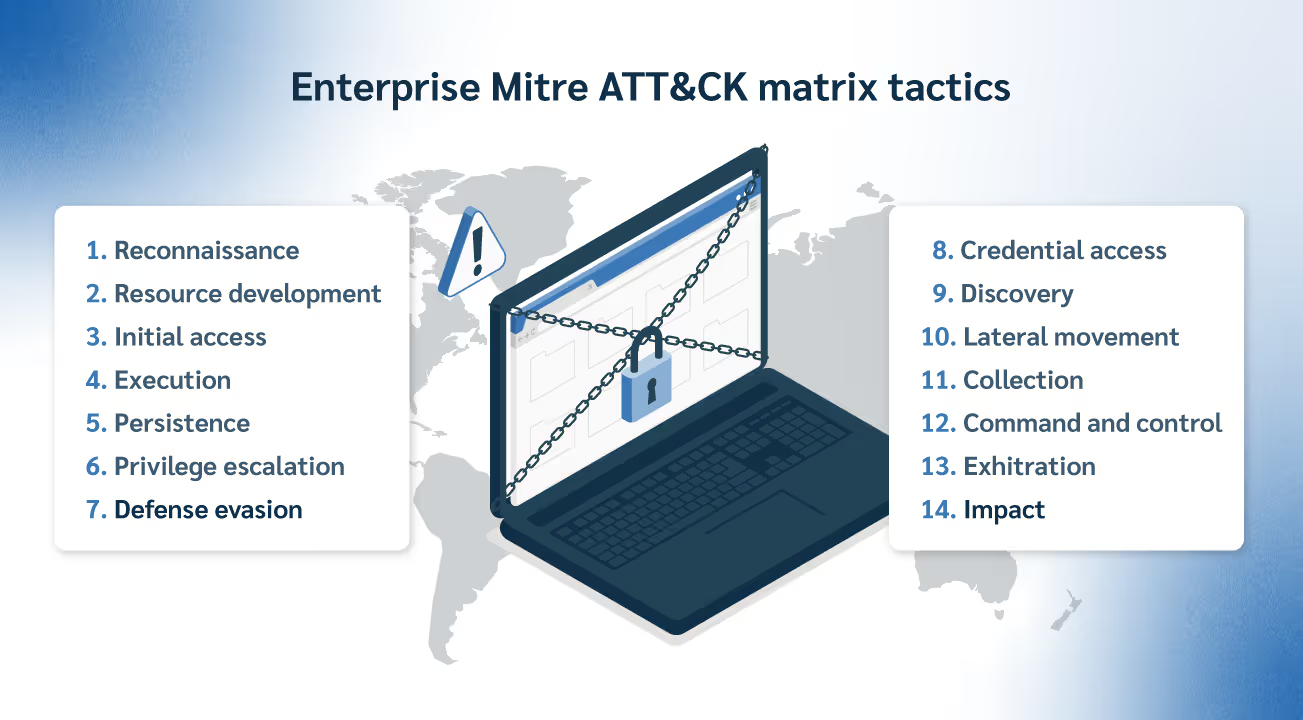
There are 14 tactics defined in the enterprise matrix, each corresponding to different stages of an attack, such as:
- Setup phase: Attackers gather information and resources that can be used to support their operations.
- Initial access: It's all about how the bad guys get their foot in the door.
- Execution: Once they have managed to get in, they need to run their malicious code to start causing damage or moving around.
- Persistence: Attackers want to stick around, even if you reboot a machine or a user logs off. This is about maintaining their grip.
- Defense evasion: To stay under the radar and achieve their goals, they need to avoid your security controls.
- Command and control: With a foothold established, the attackers move into the action phase. This stage involves controlling your system, data theft, and potential sabotage.
Understanding these tactical goals gives security teams crucial context about what attackers aim to achieve at various stages of their operations, guiding better defense and detection strategies.
Techniques
Techniques are the specific methods attackers use to accomplish their tactical goals—the "how." These include particular actions like phishing for initial access, privilege escalation via credential dumping, or encrypting data for ransom. Techniques provide security professionals clear, actionable examples of attacker behaviors, helping them directly identify suspicious activity and implement appropriate countermeasures.
Sub-techniques
Sub-techniques offer a more detailed breakdown of adversarial methods, providing even finer granularity to how attackers carry out specific techniques. For example, if credential dumping is the main technique, sub-techniques describe precise methods such as extracting credentials from memory or password stores. This extra level of detail allows defenders to pinpoint exactly how adversaries execute their actions, enhancing detection accuracy.
Procedures
Procedures refer to specific instances or real-world examples of how attackers have implemented techniques and sub-techniques during actual attacks. These include documented attack cases, malware samples, or known hacking groups' methods observed in past incidents. Studying procedures gives defenders a practical understanding of what adversary behavior truly looks like, enabling them to tailor defenses more realistically.
What is it for? Purpose and practical applications
Most threat detection tools focus on red flags after the damage is done—like malware signatures or suspicious IPs. But by then, attackers have already made their move. MITRE ATT&CK shifts the focus earlier in the chain. Instead of just tracking signs of compromise, it helps you recognize how attackers act. That behavioral insight lets teams anticipate and stop threats before things get critical.
MITRE plays a big role in making this kind of knowledge open and useful. They collect data from real incidents, organize it into a standardized format, and keep the framework updated for the entire cybersecurity community to use. That transparency helps security teams speak the same language and collaborate more effectively across companies, sectors, and even countries.
What the ATT&CK framework helps with:
- Improving threat detection: Spot suspicious behavior patterns that align with known attack techniques, even if no alert has been triggered.
- Adversary emulation: Run realistic simulations using known attacker playbooks to test how well your defenses hold up.
- Behavioral analysis: Study how attackers move through systems to uncover tactics that traditional tools might miss.
How security teams use MITRE ATT&CK
MITRE ATT&CK is a practical resource that fits into the everyday work of cybersecurity teams. It’s not just for analysts or researchers—security operations, incident response teams, and even tool developers can use it to guide decisions and actions.
Because it’s based on real-world attack behavior, it brings structure and consistency to activities that can otherwise feel reactive or disorganized. Whether you're chasing down an active threat, testing defenses, or reviewing security tools, ATT&CK offers a clear way to tie your efforts to known adversary tactics.
- Threat hunting: ATT&CK gives hunters a library of known adversary tactics to look for, helping them zero in on subtle signs that something’s off. Instead of relying on alerts alone, hunters can scan for behavioral patterns—like unusual credential use or lateral movement—that attackers often use to stay under the radar.
- Incident response: When something goes wrong, ATT&CK acts as a roadmap. It helps responders map out what techniques were used, where attackers might go next, and how to contain the damage. This structure makes it easier to piece together what happened and respond quickly with targeted actions.
- Red/Blue team exercises: Security teams use ATT&CK to plan attack simulations (red team) and defense drills (blue team). By basing scenarios on real-world techniques, the exercises feel less like guesswork and more like true training. Both sides learn more about what’s possible—and how to stop it.
- Security tool evaluations: ATT&CK gives teams a benchmark to test how well their tools perform against realistic threats. If your detection system says it can catch privilege escalation, for example, ATT&CK provides examples of how that might actually look, so you can test it with purpose.
- Security gap analysis: The framework helps security leaders see where their defenses are solid and where they’re missing coverage. By cross-referencing ATT&CK techniques with current tools and processes, teams can prioritize fixes and close gaps before attackers find them.
MITRE ATT&CK: Who needs it?
MITRE ATT&CK can benefit just about anyone working in cybersecurity, regardless of their role or specialization. It gives security professionals a common language and clear reference points to communicate threats, tactics, and defensive strategies. Different roles across cybersecurity teams leverage ATT&CK uniquely, each gaining practical insights tailored to their specific responsibilities.
SOC analysts & blue teams
For analysts actively monitoring security events, ATT&CK helps pinpoint exactly what suspicious activities might indicate. Blue teams can quickly match observed behavior—like credential misuse or lateral movement—to specific adversary techniques in ATT&CK, speeding up threat detection, refining alerts, and making investigations more precise and effective.
Threat intelligence teams
Intelligence analysts use ATT&CK as a common language to translate external threat reports into actionable insights. By mapping intelligence data to known adversary methods documented in ATT&CK, these teams can clearly communicate risks, predict attacker objectives, and prepare defenses proactively rather than simply reacting after the fact.
Red teams
Red teams rely on ATT&CK to design and execute realistic attack scenarios during penetration tests. Instead of generic simulations, they leverage the documented tactics and techniques attackers have used successfully in real breaches, giving organizations deeper insights into their actual vulnerabilities and showing defenders exactly where improvements are needed.
Security vendors
Companies developing cybersecurity products and services align their tools with the ATT&CK framework to demonstrate effectiveness clearly and transparently. Vendors can highlight precisely how their products detect, respond to, or prevent specific adversarial behaviors, helping customers evaluate and compare solutions based on real-world threat coverage.
Government & critical infrastructure operators
Government agencies and organizations managing critical infrastructure rely on ATT&CK to bolster defenses against advanced threats. Using this structured reference, they can standardize threat assessments, establish clearer communication across agencies, and enhance protection measures around critical assets, reducing the risk posed by sophisticated state-sponsored or criminal adversaries.
Operationalizing ATT&CK: Tools and resources
The MITRE ATT&CK framework isn't just a static knowledge base; it's a dynamic resource you can actively leverage with the right tools. Here are a few key players in your security toolkit that help you put ATT&CK into action:
- ATT&CK Navigator: Think of this as your interactive map of the adversary landscape. It's a web-based tool that lets you explore the ATT&CK matrices, annotate them with your coverage, and analyze attack scenarios visually. Super handy for understanding where you're strong and where the gaps might be.
- MITRE Cyber Analytics Repository (CAR): Want to move beyond just knowing what the bad guys do and actually detect them? CAR is your go-to. It's a collection of analytics designed to spot the specific adversarial behaviors detailed in ATT&CK. Think of it as pre-built threat detection rules mapped directly to the framework.
- Caldera: Caldera is an automated red-teaming platform that lets you simulate attacker behavior based on ATT&CK techniques. It's like running drills to see if you can actually identify and respond to known threats.
- Red Canary Atomic Red Team: Atomic Red Team is an open-source library of small, focused tests ("atoms") that map directly to individual ATT&CK techniques. It's a quick and dirty way to validate your detection and prevention capabilities against specific threats.
Why it matters
Traditional defenses often miss attacks because they rely on recognizing known threats rather than attacker behaviors. Behavior-based models like MITRE ATT&CK are critical because they catch threats by understanding how attackers move and act inside networks, regardless of specific malware or tools. Industry-wide adoption and global recognition of these frameworks allow better collaboration, quicker response times, and stronger overall cybersecurity worldwide.
MITRE ATT&CK stands out because it bridges strategy and execution. It gives you a clear view of how threats unfold and practical tools to respond effectively. Whether you’re building detection rules, running simulations, or analyzing an incident, ATT&CK brings structure and insight to the process. Start integrating ATT&CK into your cyber defense playbook today and make your security efforts more proactive and informed.