The 2024 Change Healthcare ransomware attack exposed 190 million patient records, making it the largest healthcare data breach in history. This devastating incident serves as a stark reminder that healthcare organizations remain prime targets for cybercriminals, with over 133 million individuals affected by healthcare data breaches in 2023 alone.
Healthcare data is exceptionally valuable on the dark web market, often selling for hundreds of dollars per record due to its utility in identity theft, insurance fraud, and prescription forgery. The healthcare sector accounts for 32% of all recorded data breaches from 2015 to 2022—nearly double the rate of any other industry. With hacking incidents causing nearly 80% of breaches and average costs reaching $15 million per incident, preventing data breaches has become a critical priority for healthcare organizations.
This comprehensive guide outlines proven strategies to protect your organization’s sensitive healthcare data, from foundational HIPAA compliance requirements to advanced threat detection systems. Whether you’re strengthening existing security measures or building a protection program from the ground up, these evidence-based approaches will help safeguard patient information and avoid the serious consequences of a data breach.
Understanding healthcare data breach risks
Healthcare organizations face a uniquely challenging security landscape. From 2009 to 2024, there were 6,759 healthcare data breaches reported, exposing nearly 847 million individual records. The trend is sharply upward—hacking incidents increased 73.4% in 2019, with ransomware attacks becoming the dominant threat vector.
Several factors make the healthcare industry particularly vulnerable:
- High-Value Target Data: Protected health information includes Social Security numbers, insurance details, medical histories, and financial information—creating a comprehensive identity theft toolkit worth significantly more than standard credit card data.
- Complex IT Infrastructure: Healthcare facilities often operate legacy systems alongside modern electronic medical records, creating security gaps that attackers can exploit. The integration of Internet of Medical Things (IoMT) devices adds additional attack surfaces.
- Broad Access Requirements: Healthcare professionals across multiple departments need access to patient information for treatment, creating challenges in managing user permissions while maintaining operational efficiency.
- Human Error Vulnerability: Over 40% of healthcare data breaches involve human error, including sending patient information to the wrong recipient, misconfigured email settings, or improper disposal incidents of paper records and electronic devices.
The financial impact extends far beyond immediate remediation costs. Healthcare data breach costs average $6.45 million, driven by regulatory fines, legal fees, patient notification expenses, and long-term reputation damage. The Office for Civil Rights has imposed penalties up to $16 million for major HIPAA violations, demonstrating the serious consequences of inadequate protection measures.
Essential technical safeguards
Technical safeguards form the foundation of healthcare data security, providing the technological barriers necessary to prevent unauthorized access disclosure and protect sensitive health information.
Data encryption
Implementing comprehensive data encryption is non-negotiable for healthcare organizations. All protected health information must be encrypted both at rest (stored in databases and on devices) and in transit (transmitted over networks). Effective encryption using standards like AES-256 renders breached healthcare records unreadable to unauthorized parties, significantly reducing the impact of security incidents.
Key encryption priorities include:
- Database encryption for electronic medical records storage
- Full-disk encryption on laptops, tablets, and mobile devices
- Email encryption for communications containing patient data
- Backup system encryption to protect archived health records
Multi-factor authentication
Two-factor authentication (2FA) or multi-factor authentication (MFA) prevents most credential theft attacks by requiring additional verification beyond passwords. Healthcare professionals accessing patient information should authenticate using something they know (password), something they have (mobile device), or something they are (biometric data).
Implement MFA on:
- Electronic medical records systems
- Administrative portals and databases
- Remote access connections
- Privileged administrator accounts
Network security measures
Network segmentation creates multiple subnetworks that contain potential breaches and limit unauthorized access to critical healthcare systems. Separate networks for medical devices, administrative systems, and patient data reduce the scope of potential damage from successful attacks.
Essential network security components include:
- Firewalls to enforce access policies at network boundaries
- Intrusion detection and prevention systems to monitor traffic for suspicious activity
- Secure VPN connections for remote access to healthcare systems
- Network monitoring tools to detect unusual data access patterns
Endpoint protection
Advanced endpoint protection goes beyond traditional antivirus to include machine learning-based threat detection, behavioral analysis, and real-time response capabilities. Healthcare organizations should deploy comprehensive endpoint protection across all devices accessing patient data.
Regular patching and infrastructure updates close security vulnerabilities that attackers often exploit. Establish automated patch management processes for operating systems, applications, and medical devices while maintaining appropriate testing protocols for critical healthcare systems.
Administrative controls and policies
While technical safeguards provide the technological foundation, administrative controls establish the governance framework that ensures consistent data protection across your healthcare organization.
Comprehensive risk assessments
Annual security risk assessments, as required by the HIPAA Security Rule, identify vulnerabilities in healthcare data handling processes and systems. These assessments should evaluate:
- Current security measures and their effectiveness
- Potential threats to patient information
- Vulnerabilities in information technology infrastructure
- Risk levels and remediation priorities
Document all assessment findings and create action plans to address identified weaknesses. Regular reassessment ensures your protection measures evolve with changing threats and organizational needs.
Access controls and user permissions
Implementing strict access controls limits patient data exposure by ensuring healthcare professionals access only the information necessary for their specific roles. Role-based access control (RBAC) systems automatically manage user permissions based on job functions, reducing administrative overhead while maintaining security.
Key access control principles include:
- Least privilege access: Users receive minimum necessary permissions
- Regular access reviews: Periodic audits ensure permissions remain appropriate
- Automated provisioning/deprovisioning: Immediate access changes when roles change
- Audit logging: Comprehensive tracking of all data access activities
Staff training and awareness
Human error remains a leading cause of healthcare data breaches, making comprehensive staff training essential for preventing data breaches. Regular HIPAA compliance training should cover:
- Proper handling of confidential healthcare data
- Recognition of phishing and social engineering attacks
- Secure email practices for patient information
- Physical security protocols for paper records and devices
- Incident reporting procedures for suspected security issues
Conduct phishing simulation exercises to test employee awareness and provide additional training for those who need reinforcement. Clear accountability measures ensure staff understand the importance of following security policies and procedures.
Incident response planning
A detailed incident response plan enables rapid containment of security incidents and minimizes damage to patient information. Your plan should include:
- Immediate response procedures for containing active breaches
- Communication protocols for notifying management and affected individuals
- Evidence preservation requirements for potential legal proceedings
- Recovery processes for restoring normal operations
- Post-incident analysis to improve future response capabilities
Test your incident response plan regularly through tabletop exercises and simulated breach scenarios to ensure all team members understand their roles and responsibilities.
Vendor and business associate management
Business associate breaches now account for a significant portion of healthcare data exposures, with over 93 million records compromised through vendor-related incidents in 2023. Healthcare organizations must implement rigorous vendor management practices to protect patient information throughout their supply chain.
Due diligence requirements
Before engaging any business associate that will handle protected health information, conduct thorough due diligence on their security practices:
- Review security policies and procedures
- Verify staff training programs and frequency
- Assess technical safeguards and infrastructure
- Evaluate incident response capabilities
- Check references from other healthcare clients
Never rely solely on vendor assurances—request documentation and consider independent security audits for critical partners.
Business associate agreements
Comprehensive business associate agreements (BAAs) legally bind vendors to maintain HIPAA-level security for patient information. Your BAAs should specify:
- Permitted uses and disclosures of patient data
- Required security safeguards and measures
- Breach notification timelines and procedures
- Right to audit vendor security practices
- Data return or destruction requirements upon contract termination
Ongoing monitoring
Vendor management doesn’t end with contract signing. Implement ongoing monitoring of business associate security through:
- Regular security assessments and audits
- Review of vendor incident reports and security updates
- Monitoring of communication channels used for patient data transmission
- Evaluation of vendor security training and awareness programs
Establish clear consequences for vendors who fail to meet security requirements, including contract termination for serious violations.
HIPAA compliance requirements
The Health Insurance Portability and Accountability Act establishes minimum security standards for protecting patient information. Understanding and implementing these requirements is fundamental to preventing healthcare data breaches.
Required safeguards
HIPAA mandates three categories of safeguards for protected health information:
Administrative Safeguards:
- Assigned security officer responsible for security policies
- Workforce training on security policies and procedures
- Information access management limiting data access to authorized users
- Security awareness and training programs
Physical Safeguards:
- Facility access controls preventing unauthorized physical access
- Workstation use restrictions limiting access to patient data
- Device and media controls for hardware containing patient information
Technical Safeguards:
- Access control measures limiting information system access
- Audit controls for monitoring access to patient information
- Integrity controls ensuring patient information remains unaltered
- Transmission security for patient data sent over networks
Documentation and reporting
Maintain comprehensive documentation of all security policies, procedures, and training activities. The Office for Civil Rights requires organizations to demonstrate compliance through detailed records during audits and investigations.
Report breaches affecting 500 or more individuals to the Office for Civil Rights within 60 days of discovery. Smaller breaches must be reported annually. Additionally, notify affected individuals within 60 days and provide information about the breach and steps being taken to address it.
Emerging threats and advanced protection
The healthcare threat landscape continues evolving, requiring organizations to implement advanced protection measures beyond traditional security approaches.
Ransomware preparedness
Ransomware attacks now dominate healthcare breach incidents, with attackers targeting both electronic medical records and operational systems. Comprehensive ransomware protection includes:
- Regular, tested backups stored offline and in multiple locations
- Network segmentation to limit ransomware spread
- Endpoint detection and response tools for early attack identification
- Employee training on ransomware delivery methods
- Incident response procedures specifically for ransomware scenarios
Never pay ransoms, as this funds criminal organizations and provides no guarantee of data recovery or protection from future attacks.
Cloud security
As healthcare organizations increasingly adopt cloud-based systems for electronic medical records and data storage, cloud security becomes critical for breach prevention:
- Verify cloud provider security certifications and compliance
- Implement strong access controls for cloud-based systems
- Ensure data encryption in cloud storage and transmission
- Maintain visibility and control over cloud-based patient information
- Establish clear data residency and sovereignty requirements
Internet of Medical Things (IoMT) security
Connected medical devices present unique security challenges due to limited built-in security features and difficulty applying traditional security measures. Protect IoMT devices through:
- Network segmentation isolating medical devices from general networks
- Regular device inventory and vulnerability assessments
- Manufacturer security update and patch management
- Strong authentication for device access and configuration
- Monitoring of device communications for anomalous activity
Continuous monitoring and threat detection
Advanced threat detection using artificial intelligence and machine learning helps identify sophisticated attacks that bypass traditional security measures. Implement continuous monitoring systems that:
- Analyze user behavior patterns for anomalies
- Monitor network traffic for suspicious activities
- Detect unusual data access or transmission patterns
- Provide real-time alerts for potential security incidents
- Integrate with security information and event management (SIEM) systems
Financial and legal preparedness
Healthcare data breach prevention requires significant financial investment, but the cost of protection remains far lower than breach remediation expenses.
Insurance and risk management
Cyber liability insurance has become essential for healthcare organizations due to the high costs associated with data breaches. Comprehensive coverage should include:
- Breach response and notification costs
- Legal defense and regulatory fine coverage
- Business interruption losses
- Reputation management expenses
- Data recovery and system restoration costs
Work with insurance providers who understand healthcare-specific risks and HIPAA requirements.
Budget planning
Security investments should be viewed as ongoing operational expenses rather than one-time purchases. Budget for:
- Regular security technology updates and maintenance
- Staff training and awareness programs
- Third-party security assessments and penetration testing
- Incident response and business continuity planning
- Legal counsel for compliance and breach response
The average healthcare organization spends 6-10% of their IT budget on security, though high-risk organizations may require greater investment.
Legal preparedness
Establish relationships with legal counsel experienced in healthcare regulations and data breach response. Legal preparedness includes:
- Understanding state and federal breach notification requirements
- Preparing template communications for breach notifications
- Developing relationships with forensic investigation firms
- Training leadership on legal obligations during security incidents
- Regular compliance reviews to identify potential violations
Continuous improvement and testing
Preventing healthcare data breaches requires ongoing vigilance and regular evaluation of security measures. Static security programs quickly become ineffective against evolving threats.
Regular security assessments
Conduct quarterly security assessments beyond the annual HIPAA requirement to ensure continuous protection improvement:
- Vulnerability scans to identify technical weaknesses
- Penetration testing to simulate real-world attacks
- Security policy reviews to ensure relevance and effectiveness
- Access audits to verify appropriate user permissions
- Vendor assessments to evaluate business associate security
Performance monitoring
Establish key performance indicators (KPIs) to measure security program effectiveness:
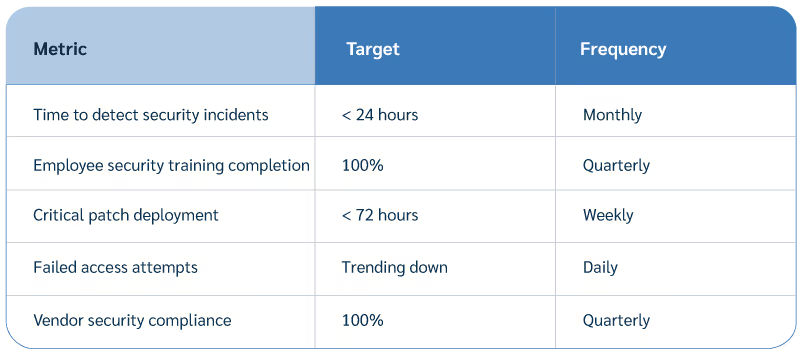
Staying current with threats
The healthcare threat landscape changes rapidly, requiring organizations to stay informed about emerging risks:
- Subscribe to healthcare security threat intelligence feeds
- Participate in information sharing organizations like Health-ISAC
- Attend security conferences and training programs
- Monitor the HIPAA Journal and Office for Civil Rights guidance
- Collaborate with trusted partners on security best practices
FAQ
What is the most common cause of healthcare data breaches?
Hacking and IT incidents cause over 64% of healthcare data breaches, with ransomware attacks being particularly prevalent. Email systems and network servers are the primary breach locations targeted by cybercriminals. Business associate breaches have increased significantly, exposing over 93 million records in 2023 alone. Human error accounts for approximately 40% of incidents, including sending patient information to wrong recipients and improper disposal of confidential data.
How much do healthcare data breaches typically cost?
Healthcare data breaches average $6.45 million in total costs, significantly higher than breaches in other industries. The cost per breached healthcare record continues rising faster than in other sectors due to regulatory requirements, notification expenses, and remediation complexity. Major breaches can result in Office for Civil Rights fines up to $16 million, as demonstrated by the 2018 Anthem penalty. These costs include investigation, notification, legal fees, regulatory fines, and long-term reputation damage.
What should organizations do immediately after discovering a breach?
Activate your incident response plan immediately to contain the breach and prevent further unauthorized access to patient information. Document all breach details including affected systems, data types, potential scope, and timeline. Report breaches affecting 500 or more individuals to the Office for Civil Rights within 60 days of discovery. Notify affected individuals within 60 days and provide clear information about the incident and protective steps being taken.
How can organizations prevent insider threats and employee errors?
Implement regular HIPAA compliance training focusing on proper handling of patient information and common error scenarios that lead to unauthorized access disclosure. Use role-based access controls limiting employee access to only necessary patient information for their job functions. Monitor user activity logs to detect unusual access patterns or policy violations that might indicate insider threats. Establish clear reporting procedures for employees to report suspected security incidents or policy violations without fear of retaliation.
What role do business associates play in healthcare data breaches?
Business associates now account for a significant portion of healthcare breaches, requiring enhanced vendor management to prevent data breaches through third-party relationships. Healthcare organizations must conduct thorough due diligence on vendor security practices and staff training programs before granting access to patient information. Business associate agreements should clearly define security responsibilities, breach notification procedures, and audit rights. Regular monitoring and auditing of vendor security practices is essential, as organizations cannot rely solely on vendor assurances about their security measures.
Healthcare data breach prevention requires a comprehensive approach combining technical safeguards, administrative controls, staff training, and continuous improvement. While the threat landscape continues evolving, organizations that implement these proven strategies significantly reduce their risk of experiencing costly and damaging security incidents.
The investment in robust security measures, though substantial, remains far less than the average $6.45 million cost of a healthcare data breach. Start by conducting a thorough security assessment of your current protection measures, then systematically implement the safeguards outlined in this guide. Remember that security is an ongoing process, not a one-time project—regular evaluation and improvement ensure your organization stays ahead of emerging threats while maintaining the trust of the patients you serve.





