As technology evolves, so too does the security that protects resources across networks. While perimeter-based security has long been the cybersecurity standard for keeping technology and assets safe, there's been a growing shift toward identity-based security approach like Zero Trust frameworks. With the ever-expanding remote workforce and increased reliance on cloud-based services and applications, IT teams can no longer rely on location to secure permissions and access to applications on a secure network.
So, what is Zero Trust? At its core, it is a security framework and philosophy model based on modern principles that's driving the new age of network protection and providing tighter monitoring of applications and data. Zero Trust network access (ZTNA) utilizes technologies that build upon the principles and philosophy of Zero Trust policies to implement a comprehensive and continuous network of security protocols for greater protection from cyber threats, such as hackers and malware. Whereas a virtual private network (VPN) stands between the end user and a network, Zero Trust network access (ZTNA) stands between the user and the applications on the network. This restricts access to all users, regardless of whether or not they have access to the resident network.
In a Zero Trust security system, the name says it all—nobody is trusted without verification. Learn more about the core Zero Trust technology, principles, and philosophy as well as the key elements for implementing a Zero Trust model for your company.
The principles of Zero Trust
In a Zero Trust framework, the principles are the guiding beliefs and ideas that underpin the overall approach. Without an understanding of the principles, it’s hard to maintain a systematic approach across a company with varying degrees of security access and privileges. Using the principles, IT security teams can standardize how they verify access as well as who gets access to specific applications and resources. They can also use these principles to create guidelines to help each person know how to identify a threat and restrict access.
There are three key principles within a Zero Trust policy. They include:
- Explicit monitoring
- Apply least privilege access
- Assume breach
The first principle of the Zero Trust model is summed up in four words: never trust; always verify. It relies on identifying the user and their device—each and every time they log on to an application to ensure no new threats have been introduced. Monitoring continues throughout the use, and if any threat is detected, new verification will need to occur.
This is done through authentication, which in the Zero Trust model can use multi-factor authentication (MFA), identity and access management (IAM), and endpoint security tools to authenticate user identities is). Other multi-factor steps might include fingerprint identification or facial recognition.
The Zero Trust least privilege principle limits users to applications for which they have privileges. If a user doesn't have access or authorization to an application or service, the application service is either grayed out, so that nothing happens if they try clicking on it, or the restricted resource is hidden from the user entirely. By employing role-based access controls (RBAC), privileges can be delineated according to a user's function and their access will be modified based on their privilege.
For example, a company may use an all-encompassing application to access employee payroll, employee performance records, company finances, and marketing strategies. A Zero Trust approach makes sure that a payroll accountant is unable to access employee performance records, while an office supervisor would likely be unable to view payroll records or company finances.
To get access to an unauthorized application, the user will need to reverify themselves again with updated privilege settings. Once accessed, a user can only utilize the minimal functions necessary to accomplish their tasks.
The third principle reminds admins that a breach is always a possibility. Since many active network infiltrations are attacks of opportunity, proactive measures based on this principle—like continual monitoring and anomaly detection—can alert administrators of potential threats before they become detrimental.
Measures such as these also provide metrics that enable administrators and engineers to quickly adapt to newer threats. When combined with other principles and passive operations—such as least privilege access functions—networks become less desirable for would-be trespassers to attempt entry.
The Zero Trust principles build the guiding concepts for a complete cybersecurity model. They remind IT, teams, why they are trying to continuously improve their security posture, reduce the risk of data breaches, and easily adapt to evolving threats. Adding in the philosophy behind the Zero Trust security model is the next step to creating a holistic security strategy.
Philosophy: the Zero Trust security model
The Zero Trust security model (ZTSM) is the conceptual framework built off of the guiding principles that Zero Trust systems employ in practical operation, enabling an organization to address risks and vulnerability threats as they arise. The Zero Trust security model is built on core tenets that guide the construction of comprehensive security solutions.
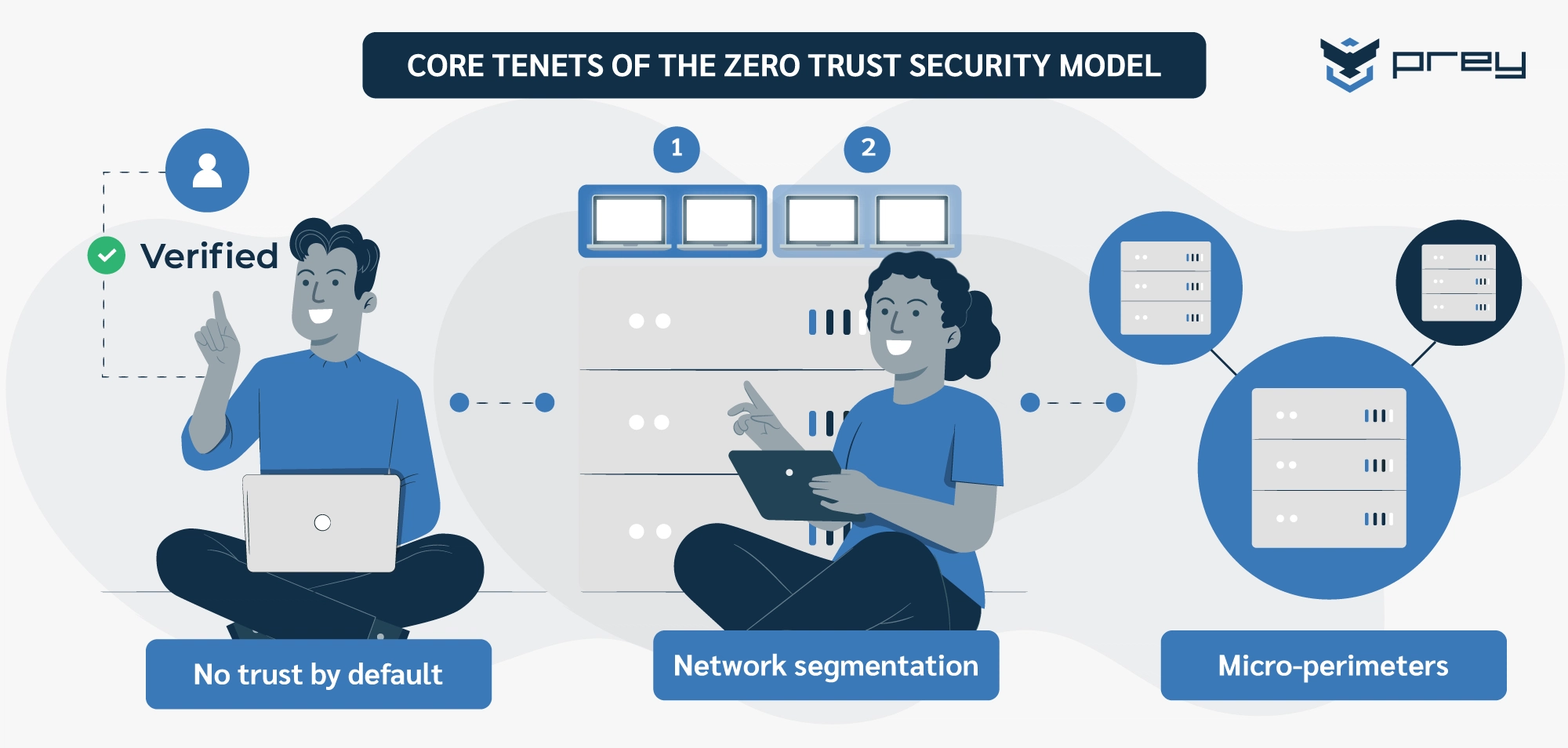
Core tenets of the Zero Trust security model
There are 3 core tenets that build the philosophy of the Zero Trust security model. They are:
- No trust by default
- Network segmentation
- Micro-perimeters
The core tenet of the Zero Trust security model is to never trust and always verify. If a user has gained access to one application or service, it doesn't mean they have access to all applications. The user will need to reverify their identity, context, and security posture for each application they wish to enter.
Zero Trust continuously monitors for any change in a user's identity, context, or security posture throughout the life of a session too. If a user is logged in to an application but hasn't used it for a certain amount of time, they may get automatically logged out based on inactivity. This is to ensure that an unauthorized person can't gain access if the user has left their computer.
A highly effective element in a comprehensive Zero Trust network security strategy is network segmentation. The practice of dividing a larger system into smaller, isolated networks operating independently minimizes risk if there's ever a breach.
One effective method of segmenting a network is to employ virtual local area networks (VLANs), which isolate the segments and restrict access between them. These silos help keep would-be infiltrators separated from the rest of the larger system.
Silos can be further protected by micro-perimeters. Focused boundaries around specific assets within segments provide an added layer of protection to sensitive databases. Micro-perimeters (also called micro-segmentation) extend that protection further by isolating an application or service from other resources within the same silo. This layering of security greatly reduces possible attack points and leads to a more secure IT environment.
Importance of Zero Trust security model
From ransomware to supply chain attacks to user error, data breaches can come from anywhere. According to NIST, 1 in 5 small businesses report experiencing a cyber attack, which can lead to disastrous results.
Even the largest companies are not immune. Attacks such as Verizon's 2021 data breach have made it clear that a robust, comprehensive, and agile network security model like Zero Trust is crucial in deterring and eliminating potential threats. Since cyber attacks evolve daily, it makes a Zero Trust security model more vital for a company of any size to be able to address modern cybersecurity concerns.
Plus, standardized and vigilant security strategies improve a company’s overall security posture and IT environment. The security posture philosophy verifies the safety of a user's device. A Zero Trust system checks to make sure certain elements are in place — such as verifying an OS is up to date or that the user's computer has appropriate anti-malware software installed and running before allowing access. By ensuring all connecting devices are as secure as possible, the security posture of the company is protected as well.
Implementing the Zero Trust security model
Many vital components go into the implementation of all cybersecurity models. The more assets and critical systems that are identified and addressed during implementation, the more success your security measures will have in protecting them. Below are some of the fundamental steps to implementing a Zero Trust security model.
Determine critical assets
Identify the important data and assets within your network that require strict protection. Personal medical data and banking information are good examples of assets that could negatively impact an organization if compromised.
Then, continue assessing the rest of your assets, classifying them, and start determining privilege levels.
Network traffic control
Set up routing on the network to direct users to specific network locations on entry. Rather than logging into the network system itself, user requests are funneled directly to the database or application for logging in.
Build or configure a network for Zero Trust
Install VLANs or other network segmentation applications and micro-perimeter security to silo critical environments and implement robust authentication measures, such as MFA.
Adopt a Zero Trust security policy
Identify which users should have access to which assets and to what extent. Configure the system to only allow users access to resources necessary to complete required tasks.
Make sure all users are set up with MFA access. Monitor and report on all activity, especially anomalous events including attempts to invade the system. Activity logs and analytics are wonderful tools for identifying and analyzing potential threats.
Implementation challenges
Implementation of any security model is going to have challenges. When putting a Zero Trust system in place, it’s helpful if organizations can expect certain barriers and understand how to fix them.
User experience is essential, and it may take some trial and error to optimize it within a Zero Trust model. For example, frequent session timeouts might impede a customer service rep's ability to efficiently do their job. Balancing timeouts with the rep's workflow can dramatically improve the user experience, while also ensuring a secure system.
Integrating Zero Trust technology with existing systems might also prove challenging. Administrators that understand the current systems are tremendous resources when it comes to finding the right solution for an organization. With some research and cooperation between the existing knowledge at an organization and the new security solution provider, a company can ensure a seamless transition.
Technology: Zero Trust network access (ZTNA)
Zero Trust network access (ZTNA) refers to the actual technology that utilizes the Zero Trust model for security. There is no single ZTNA software or security provider. Instead, a number of organizations employ completely different Zero Trust technologies to enable secure access to applications and services without exposing them to the broader network, preventing unauthorized access and minimizing potential attack vectors.
The ZTNA system may be a network application or a piece of network hardware with a built-in firewall. Many cloud-service providers already employ ZTNA technology, making onboarding much easier for enterprises to integrate. However, additional security layers, like a VPN, are not discouraged.
How ZTNA works
ZTNAs employ their applications or devices to start acting as "trust brokers" to verify user identities and privileges. The trust broker's number-one priority is to restrict access on a granular level to minimize potential points of access and prevent unauthorized entry, greatly reducing vulnerability to attack.
ZTNA technologies will only grant access to authorized users after they've verified their identities and the trust broker has determined the user's device meets all security requirements. The broker only allows authorized users to access resources that are specific to the user through RBAC contexts set up within the network to determine which users can access specific databases and applications.
Once a user is in, the trust broker continues to monitor in the background and assess any changes to user identity, usage, and system requirements. Any change that falls outside of security parameters usually results in the removal of the user from the app. They may even get locked out, depending on the ZTNA system.
Benefits of ZTNA
Employing Zero Trust network access greatly enhances a company’s system security. It also allows for seamless, secure access from any device anywhere in the world. With the trust broker standing between users and network resources, critical assets are left virtually invisible to unauthorized users. If an unauthorized user happens to become aware of a critical asset, the broker's access controls shut down any attempts at entry.
Another benefit of ZTNA is simplified access management. Zero Trust security systems and policies lay out all of the guidelines for access and enable organizations to centralize permissions and streamline security processes. This makes the work of monitoring and maintaining network security much easier for administrators, who can focus on adapting the system as needed.
Lastly, Zero Trust network security provides greater productivity for users. It may seem like an overwhelming system, but its ability to seamlessly integrate to any device from anywhere in the world allows employees to have the same experiences and access from any place they work.
Real-life examples of Zero Trust
Organizations everywhere are securing their networks with Zero Trust cybersecurity models and technologies. The reliability and peace of mind that Zero Trust offers make it just as ideal for smaller enterprises and medium-sized organizations as well.
Google's BeyondCorp
Google's Zero Trust model comes from years of expertise within company personnel combined with ideas from user experiences. Through user input and company knowledge Google was able to build their ZTNA technologies called BeyondCorp from the ground up, piece by piece. The result is a robust system that grants user access based on contextual factors, irrespective of the network the user accesses Google services from.
For example, when a user sets up a Google account, their available access is determined by the Google services they acquire. By authenticating, Google provides an encrypted tunnel only to the Google resources the user has signed up for and downloaded. A user's Google Drive, documents, and spreadsheets are only available to them and invisible to anyone else logged into Google. The user can opt to share a document or drive access, which they also have the ability to revoke at any time.
DZ Bank
DZ Bank AG is one of the most preeminent private financial services organizations in Germany. This institution made the decision to move away from a perimeter model and toward a Zero Trust model to segment its network, isolate customer accounts from potential cyber infiltrators, and give users better control over their accounts.
The key challenge for DZ Bank has been integrating the Zero Trust solution with its existing infrastructure. By setting up large-scale cloud environments, the bank's service provider was able to establish Zero Trust protection between their on-site environment, cloud environments, and the end users.
Other financial institutions and Zero Trust
Even though it's proven disastrous for a number of financial institutions, banks, and other financial organizations are hesitant to move away from the classic "castle and moat" perimeter-security model.
Equifax's 2017 breach is a clear case of how a Zero Trust model might have prevented a devastating attack. Hackers were able to exploit a flaw in the web design of the company's customer complaint portal. From there, the intruders were able to move onto the broader network and scope for sensitive data.
Had the system been segmented into isolated silos, requiring authentication for access beyond the breach point, the hackers would have been stopped by each micro-perimeter. Instead, they walked away with immense amounts of sensitive data and credit history from Equifax—putting the financial well-being of millions of people at risk.
Administrators everywhere already understand the impact a Zero Trust approach can have on an organization and are pushing for executive buy-in. The lessons learned from Google’s successful implementation using expertise and user input as well as evidence of the issues Equifax faced because they didn’t evolve into a robust Zero Trust system might help business owners see the value in updating to a new security model.
The future of Zero Trust cybersecurity
Remote work is here to stay for many organizations. As such, machine identities are growing at a much higher rate than human identities in the digital landscape. As users move between their phones, tablets, and computers throughout the workday, Zero Trust ensures that they have a secure connection to their work resources across all devices.
The growing plane of user and machine identities provides an excellent opportunity for developers to incorporate artificial intelligence (AI) into their Zero Trust security measures. AI has the potential to further expand monitoring to elements beyond current verification methods. For example, machine learning might enable the trust broker to recognize changes in work habits such as typing rhythm. This could allow the system to detect a possible unauthorized user and require re-authentication before continuing.
Takeaways
Modern digital threats are always evolving. That’s why a robust and agile network security policy is essential to ensure the safe operation of network resources. By using multi-factor verification, segmenting networks, isolating assets, and inserting a trusted broker between applications and end users, Zero Trust security models keep intruders out and ensure organizations and users alike will be able to interact safely.
Implementing Zero Trust into a comprehensive security strategy—which may also include VPN or perimeter security measures—helps IT admins more quickly address key vulnerabilities and potential risks in their IT environment by shutting compromised users out of the system. By looking at real-life Zero Trust systems within large organizations, learning more about the policies and philosophies behind the enhanced Zero Trust model, and hiring the right team to implement, monitor, and update the technologies, any company can build a Zero Trust cybersecurity policy to protect their most valuable assets and resources.
To get started with Zero Trust for your company, dive into the key components of a Zero Trust model and how to adapt the principles to a specific company’s needs. Then, learn more about the different ZTNA technologies in more of our detailed Zero Trust guides and series.






