According to Verizon’s 2025 Data Breach Investigations Report (DBIR), K–12 schools faced over 1,075 security incidents, with 851 resulting in confirmed data breaches. These attacks weren’t just random — ransomware, social engineering, and system intrusions were the leading culprits. Yet, despite the growing threat, many schools are still under-resourced and lack the cybersecurity expertise needed to keep up. With 88% of breaches financially motivated, it's clear attackers see schools as easy, valuable targets.
So, what's an already swamped IT team to do? One of the smartest moves you can make is to lean on proven cybersecurity frameworks. Think of them as a lifeline in the choppy waters of cyber threats. They offer a clear, step-by-step way to figure out what needs protecting most, build up your defenses bit by bit, and know what to do when (not if) something goes sideways. Whether you're a one-person IT show or have a small but mighty team, these frameworks give you a fighting chance to secure your district without having to reinvent the wheel.
What are cybersecurity frameworks?
Cybersecurity frameworks are like these food recipes or detailed LEGO instructions: they guide you step-by-step without locking you into one rigid way of doing things. At their heart, these frameworks are well-organized collections of best practices and guidelines designed to help you tackle and shrink those ever-present cybersecurity risks. They're like having a seasoned guide who's been through the cyber trenches, offering a solid starting point so you're not just flailing around in the dark.
Now, not every framework is a one-size-fits-all deal. Some help you zoom out and map your overall security strategy – the big picture stuff. Others get down in the weeds, offering practical advice for daily protection and keeping your systems humming. And some are like threat intelligence briefings, showing you how the attackers think so that you can anticipate their moves. For K-12 schools, these frameworks are gold because they help you:
- Build a solid foundation for your security efforts, even if you're starting from scratch.
- Figure out where to spend your precious time and budget for the biggest impact.
- Spot and deal with threats faster and more effectively, because let's face it, time is never on your side.
- Talk about risks and what you're doing with everyone, from the superintendent to the school board.
K12 SIX Essential Cybersecurity Protections
For K-12 school districts navigating the complex landscape of cybersecurity with often limited resources, the K12 SIX Essential Cybersecurity Protections (ECP) framework offers a practical and focused starting point.
K12 SIX is a nonprofit cybersecurity community built specifically for K–12 school districts. Created by a group of practicing IT leaders from the education sector, K12 SIX focuses on giving schools practical tools to defend against cyber threats. Their "Essential Cybersecurity Protections" list was designed to offer straightforward, high-impact steps that schools of all sizes can realistically implement, even when budgets and staffing are tight.
How it works
The K12 SIX ECP framework is updated every year to reflect the latest threats and best practices. The 2024–2025 edition organizes protections into five main categories, each with specific subcategories that spell out exactly what schools need to focus on—making it much easier to break big security goals into achievable tasks. It’s not about perfection; it’s about taking meaningful, manageable steps toward better protection.
For example, under the first category, 1.0 Sanitize Network Traffic to/from the Internet, schools are encouraged to block malicious websites, defend against phishing and email scams, and segment critical services to limit exposure. Instead of just telling schools to "secure your network," it offers specific, actionable controls that make a real difference without overwhelming IT teams.
What it brings to K–12 tech teams
- Practical, easy-to-adopt protections tailored for resource-constrained environments: Focuses on what schools can realistically achieve, not just ideal scenarios.
- A good “first step” for districts that can’t adopt broader frameworks right away: Helps schools get started with cybersecurity without needing a full-time security team.
- Helps reduce risk from the most common attacks: Targets the biggest threats schools face, like phishing, ransomware, and unauthorized access.
- Updated yearly to address newer cybersecurity threats: Ensures schools are working with current, relevant advice—not outdated checklists.
Learn more about how to implement K12 six ECP framework in your school
CIS Critical Security Controls (CIS Controls)

The CIS Critical Security Controls come to us from the Center for Internet Security (CIS), a non-profit organization dedicated to making cybersecurity practical, accessible, and effective for organizations of all sizes. Their mission resonates particularly well with the challenges faced by K-12 schools, often needing robust security without the complexity or overhead of enterprise-level solutions.
Think of the CIS Controls as a prioritized, focused to-do list for cybersecurity. Instead of being overwhelmed by a massive list of potential security measures, the CIS Controls offer a curated set of actions that, when implemented, provide significant defense against the most common and damaging cyber threats. Schools, governments, and businesses around the world rely on them because they're grounded in real-world experience and are designed to be scalable, fitting organizations with varying levels of resources and technical expertise.
How it works
The CIS Controls (V8) are divided into 18 specific safeguards, each addressing a different part of cybersecurity—everything from asset management to access control and incident response. What makes them especially useful is the concept of Implementation Groups (IGs), which tailor the controls to different levels of organizational maturity and risk.
Let’s say a school wants to take its first real step into cybersecurity without overloading its small IT team. Implementation Group 1 (IG1) is the perfect place to start. It includes a focused set of actions—like keeping an updated inventory of devices, applying security updates, managing user accounts, and backing up data. These may seem basic, but they can dramatically shrink a school’s attack surface and stop many common threats before they even get a foothold.
Here’s a quick breakdown of the 3 different Implementation Groups (IGs):
- IG1: Tailored for small or resource-constrained organizations, this group focuses on essential, high-impact actions that offer the most protection for the least complexity. For K–12 schools, it’s a realistic and effective place to start without overwhelming IT teams.
- IG2: Aimed at organizations with more IT staff and moderate risk levels, IG2 adds deeper layers of protection, including stronger access controls, data encryption practices, and more structured vulnerability management.
- IG3: Designed for large or high-risk entities like government agencies or critical infrastructure providers, IG3 covers advanced security operations, continuous monitoring, and robust incident response—ideal for institutions with mature cybersecurity programs and dedicated teams.
What it brings to K–12
- A practical, step-by-step guide for schools to build up their defenses: The CIS Controls break down the often overwhelming task of cybersecurity into manageable and actionable steps, making it easier for IT teams to make tangible progress without needing to overhaul everything at once.
- Scales with your resources, allowing you to start small and grow as your capabilities improve: Thanks to the Implementation Groups, schools can begin with the essential controls in IG1 and gradually implement more advanced safeguards as their team, budget, and understanding of their risk evolve.
- Helps align with other frameworks and compliance requirements: The CIS Controls are often mapped to other well-regarded frameworks like NIST CSF and CISA’s Cyber Performance Goals, making it easier to demonstrate compliance and ensure consistency across different security standards.
- Supports audit readiness and provides clear implementation guidance: Whether you're facing state audits, insurance reviews, or simply want to demonstrate a commitment to security, the CIS Controls offer well-documented steps that can help you prepare and showcase your security efforts.
Learn more about how to decode the CIS control framework for k-12 tech teams
NIST Cybersecurity Framework (NIST CSF)
The NIST Cybersecurity Framework (NIST CSF) was developed by the National Institute of Standards and Technology to help organizations build smarter, more resilient cybersecurity programs. Originally created for critical infrastructure like energy and transportation, it quickly proved flexible enough to benefit any sector, including education. At its heart, it’s a risk-based framework. This means it's designed to help you focus on what truly matters for your district without getting bogged down in unnecessary complexities.
How it works
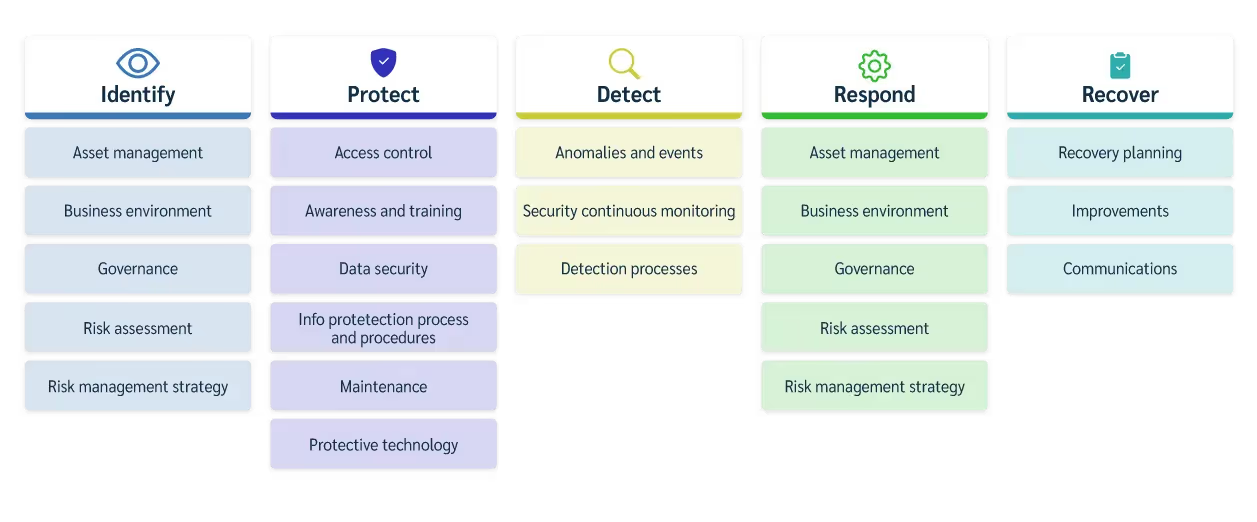
The NIST CSF is organized into five core functions: Identify, Protect, Detect, Respond, and Recover. Schools can use these pillars to evaluate where they stand today, define where they want to be, and chart a clear path forward. It's a living guide, and it plays nicely with other compliance efforts and security programs, making it easy to align with existing regulations or future requirements.
Imagine this in a school setting: First, you figure out (Identify) where all that sensitive student data lives. Then, you lock down who can access it (Protect). Next, you set up alerts to flag any unusual login attempts (Detect). If something looks off, you jump into action to block the threat (Respond). And finally, if any systems are affected, you restore them from clean backups (Recover). It’s a continuous cycle, making security an ongoing process, not just a one-time checklist.
What it brings to K–12 tech teams
- A strategic foundation to build a district-wide cybersecurity program: This framework provides a structured approach to building your defenses, helping you move beyond simply reacting to the latest threats and develop a more proactive, long-term strategy.
- Helps clarify roles, set priorities, and guide long-term planning: For IT teams often juggling multiple responsibilities, NIST CSF offers a clearer roadmap and facilitates better communication and alignment with school leadership on cybersecurity goals.
- Works well for schools starting to formalize cybersecurity efforts: If your district is transitioning from ad-hoc security measures to a more structured approach, NIST CSF offers a robust yet adaptable framework to build a sustainable and scalable security posture.
Learn more about it in our NIST guide for k-12 tech leaders.
MITRE ATT&CK Framework
Let's be upfront: diving into the MITRE ATT&CK Framework can initially feel like plunging into the deep end of the cybersecurity pool. It's a comprehensive and incredibly detailed knowledge base meticulously documenting exactly how real-world attackers behave once they've infiltrated a system. For already stretched K-12 IT teams, the sheer volume of information can seem daunting. However, understanding ATT&CK is increasingly becoming a must-have in the fight to protect our schools.
This globally trusted framework, developed by MITRE, a non-profit supporting U.S. government and private sector cybersecurity efforts, documents the practical, observed tactics that hackers actually use. Instead of solely focusing on the 'what' after an attack, ATT&CK digs deep into the critical 'how' and 'why' behind their actions.
How it works
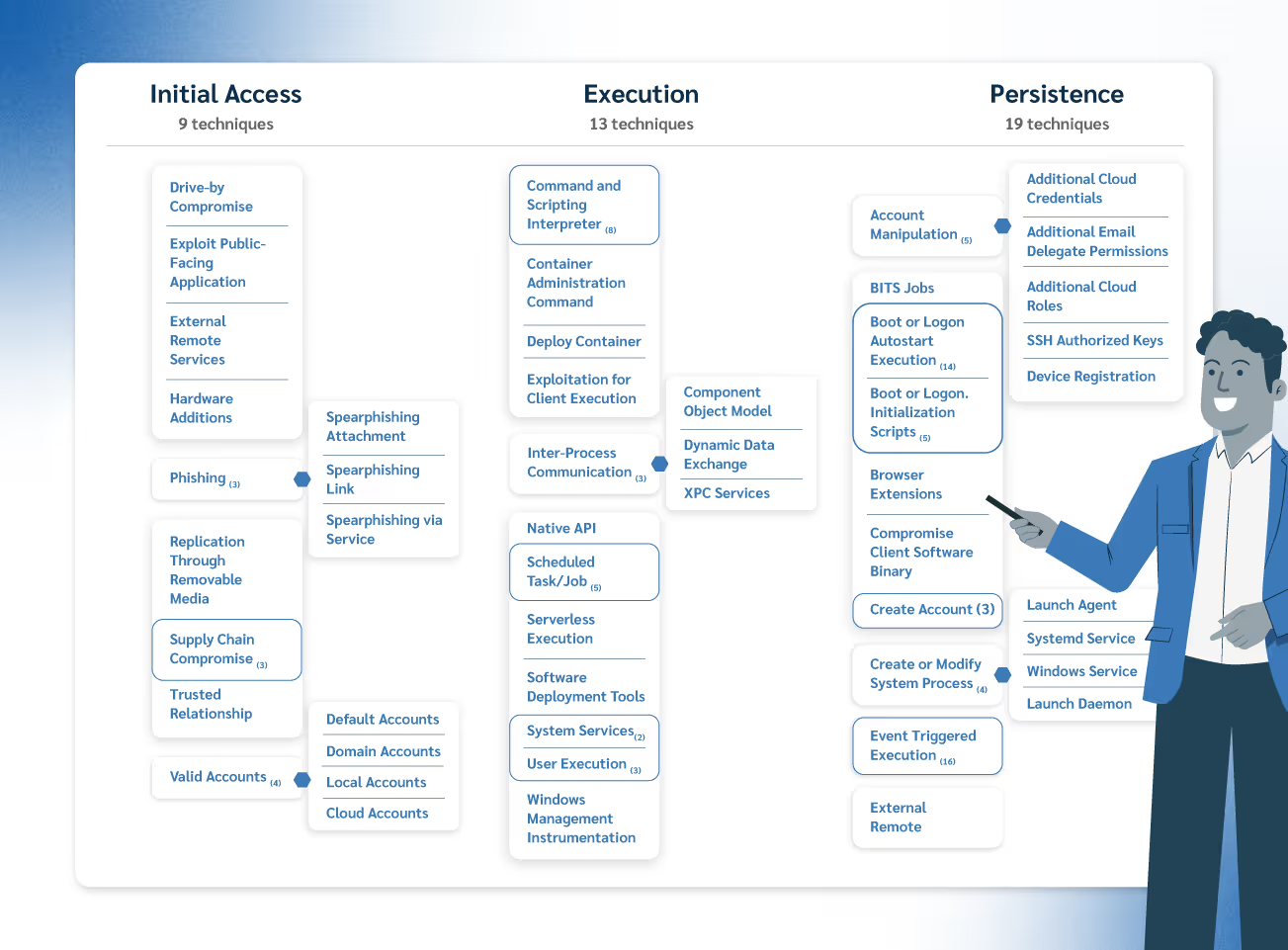
MITRE ATT&CK organizes its knowledge into matrices for different environments, like Enterprise systems (your main school network), Mobile devices (those student devices that roam in and out of your control), and Industrial Control Systems (ICS). Each matrix maps out the tactics, techniques, and procedures (TTPs) that real threat actors use during their attacks. It’s a living project, too—updated regularly with contributions from cybersecurity researchers, analysts, and practitioners around the world to stay sharp and current.
Consider the Enterprise matrix. It meticulously breaks down the many ways an attacker might try to navigate your school's network. This could range from seemingly innocent phishing emails designed to steal credentials to more sophisticated techniques like exploiting software vulnerabilities or establishing hidden communication channels. By understanding these step-by-step attacker behaviors, your IT team can move beyond simply reacting to alerts and start proactively looking for the tell-tale signs of an attack in progress, potentially stopping a breach before it even fully unfolds.
What it brings to K–12
- Empowers IT teams to detect threats earlier by understanding attacker behavior, not just relying on traditional alerts: This knowledge allows for a more proactive security posture, enabling even resource-constrained teams to look for suspicious patterns and potentially prevent significant incidents.
- Provides valuable insights for more advanced security discussions with vendors and partners: Even if your internal team is lean, understanding ATT&CK's language and concepts can lead to more informed conversations with security vendors, ensuring you're getting solutions that truly address the threats you face.
- Offers a framework for realistic security training and simulations: For schools looking to improve their incident response capabilities, ATT&CK provides a structured way to simulate real-world attack scenarios, helping your team practice their procedures and build confidence in their ability to respond effectively.
Learn more about the MITRE ATT&CK framework for K-12 setting
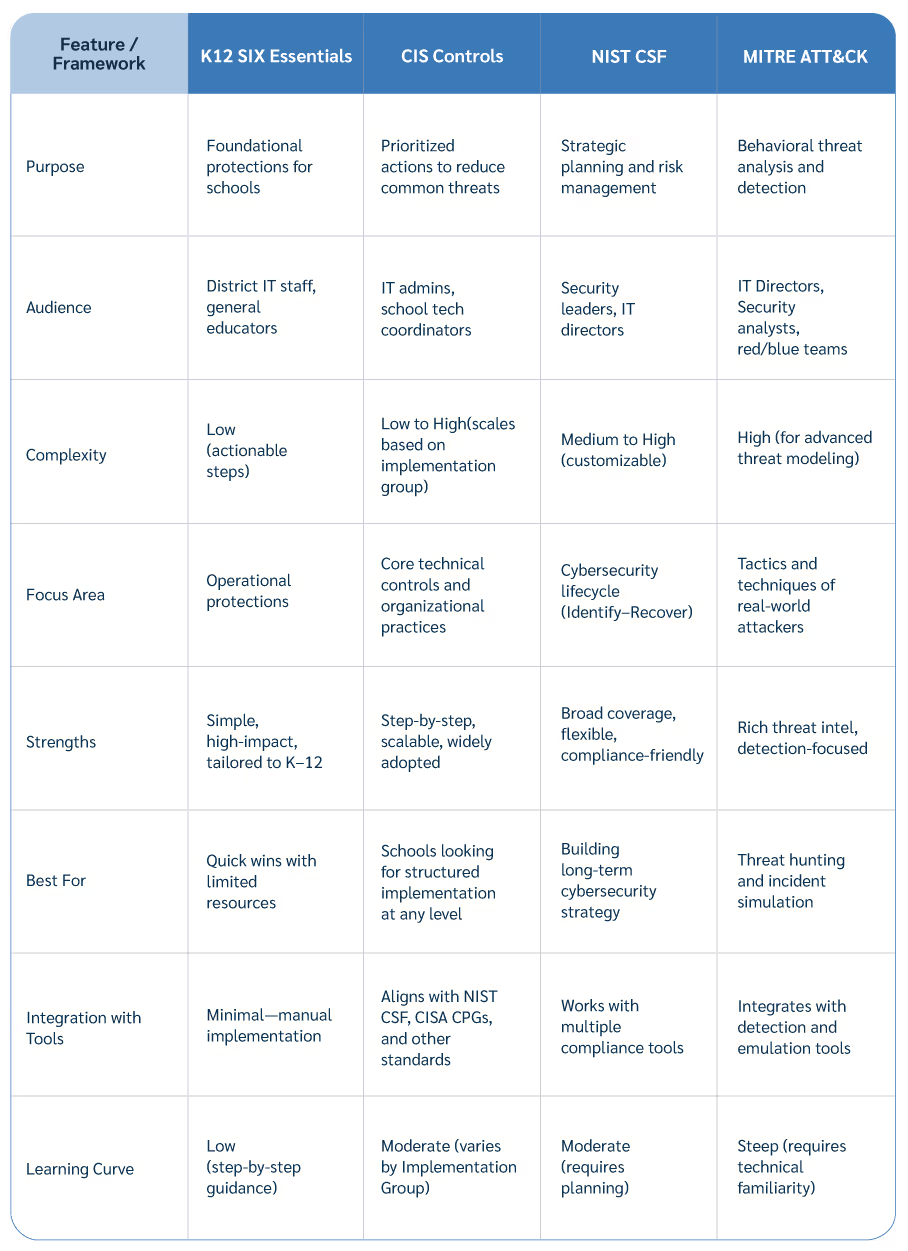
Framework comparison table
We've walked through a few key cybersecurity frameworks, and you might be wondering, "Okay, but which one is right for us?" The truth is, there's no single "best" framework for every school district. Your ideal choice will depend on factors like the size of your IT team, your budget, your current security maturity, and the specific risks you face.
Finding your starting point (and your path forward)
It's important to remember that you don't have to pick just one framework. In fact, many schools find that a layered approach, combining elements from different frameworks, provides the most robust defense.
Think of it this way:
- K12 SIX can be your go-to for those immediate, essential security actions that provide a strong baseline level of protection, especially when time and resources are tight.
- CIS Controls offer a practical, step-by-step roadmap for implementing critical security controls, allowing you to gradually mature your security posture based on your resources and needs through the Implementation Groups.
- NIST CSF can serve as your overarching strategic guide, helping you map out your long-term cybersecurity goals, prioritize risks, and align your efforts with broader compliance requirements.
- MITRE ATT&CK can be invaluable for understanding the specific ways attackers might target your school, informing your threat detection strategies and helping you train your team for realistic scenarios.
Ultimately, the goal isn't to perfectly implement every aspect of every framework overnight. It's about starting smart, making consistent progress, and choosing the frameworks and controls that best address your school district's unique challenges and priorities. Every step you take towards a more structured approach to cybersecurity, no matter how small, makes a difference in protecting your students, staff, and data.
Building a safer school, one framework at a time
The world of cybersecurity can feel overwhelming, especially when you're already dealing with a million other things in your school. The good news is, you don't have to conquer it all at once. Think of these frameworks not as insurmountable mountains, but as helpful maps and guidebooks for your journey toward a more secure school environment.
Many districts find that the most effective approach is to start with the foundational, actionable steps offered by K12 SIX to quickly address those high-priority vulnerabilities. From there, you can begin to weave in the strategic planning of NIST CSF to build a more comprehensive and adaptable security program over time.
As your team's expertise and your security posture mature, incorporating the threat intelligence of MITRE ATT&CK can provide invaluable insights into how to better detect and respond to sophisticated attacks. And the CIS Controls? They offer that practical, step-by-step implementation guidance that scales with your resources, ensuring you're always making tangible progress, no matter your starting point.
The key takeaway here is that progress, not perfection, is the goal. Every step you take to implement these frameworks, whether it's adopting a few essential controls from K12 SIX, starting to map your assets with NIST CSF in mind, or even just familiarizing yourself with the common attacker tactics in MITRE ATT&CK, contributes to a safer digital environment for your students and staff.
You're not alone in this challenge. Lean on the resources provided by these frameworks, connect with your peers in the K-12 IT community, and celebrate the small victories along the way.
Building a resilient and secure school district is a marathon, not a sprint. Start smart, stay consistent, and know that every effort you make has a real and meaningful impact on protecting your educational mission.