Credentials are the new gold on the dark web—a valuable currency that fuels an underground economy that’s as complex as any legitimate business. Welcome to the murky world of the credentials black market, where stolen usernames, passwords, and personal data are auctioned, sold, and traded like hot commodities.
Hence, in this post, I’ll dive into the hierarchy that governs this illicit market, exploring how credentials are ranked, distributed, and used to fuel cybercrime on a global scale. Buckle up: you’re about to get a front-row seat to the digital underworld.
Understanding the ecosystem: From phishers to brokers
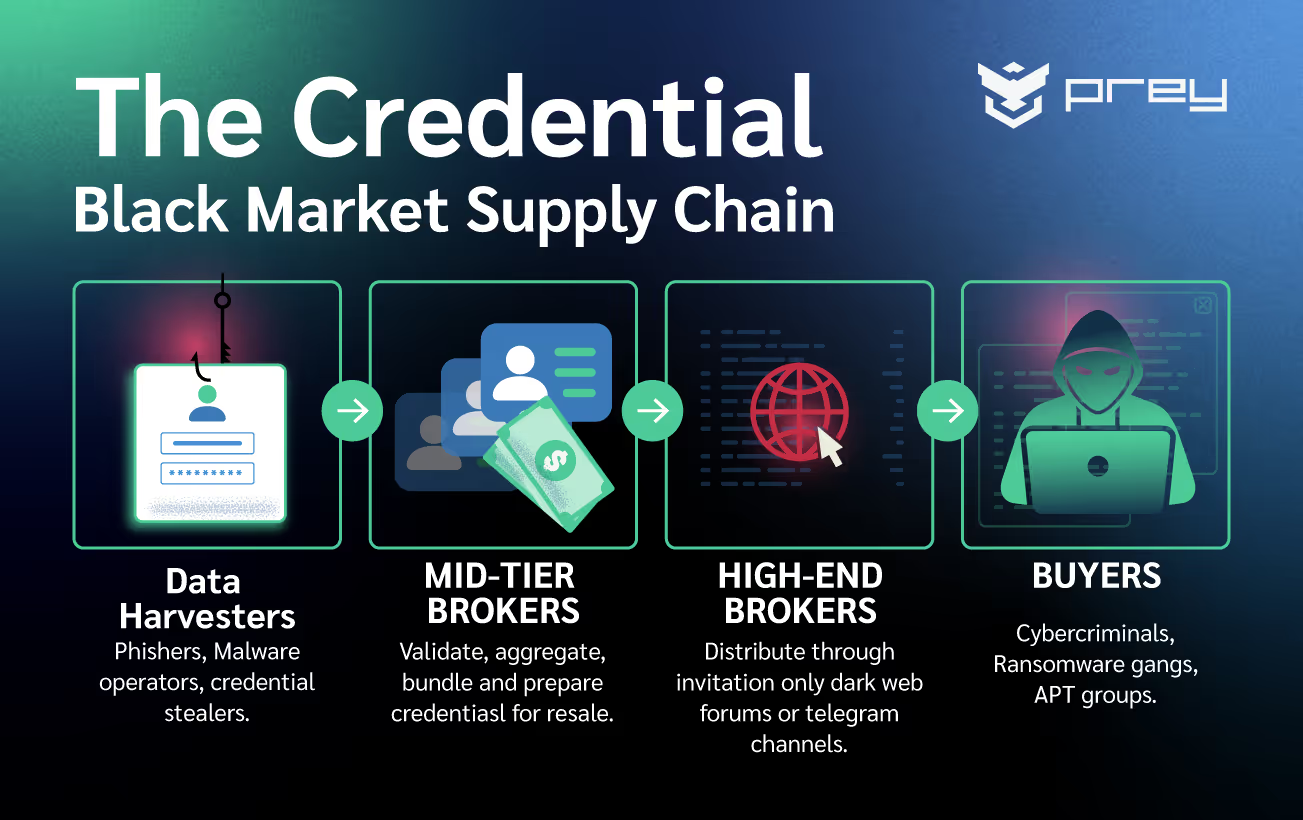
The black market for credentials isn’t just a single website or shady Telegram channel—it’s a layered, well-oiled machine. It all starts with data harvesters: the phishers, malware distributors, and hackers who collect credentials in large quantities. These actors are the ground-level suppliers in the threat actor hierarchy, often targeting everything from small businesses to unsuspecting individuals.
Once harvested, the credentials rarely stay with the same person for long. They move up the chain to mid-tier access brokers, who specialize in aggregating, verifying, and packaging these credentials into easy-to-sell bundles. These brokers might add value by categorizing the data—separating corporate logins from social media credentials, for example—or by checking credentials against known breaches to assess their freshness.
At the top of the hierarchy sit the high-end brokers and marketplaces. These are the power players who run invitation-only forums and dark web platforms, selling credentials to buyers who might be cybercriminal gangs, ransomware operators, or even state-sponsored hackers. These buyers rely on brokers for curated, high-quality data that can fuel everything from account takeovers to targeted phishing campaigns.
Freshness and quality control: The black market’s QA process
One of the most fascinating—and alarming—facets of the credentials black market is its surprisingly sophisticated quality control mechanisms. Think of it like a shady Amazon, where customer satisfaction still matters. The concept of “freshness” is paramount: credentials lose value quickly if the rightful owner changes their password or if a breach is widely reported.
To maintain profitability, sellers often test credentials to ensure they work. Fresh credentials are especially sought-after for orchestrating supply chain attacks, where gaining initial access can compromise an entire network or partner ecosystem. Some marketplaces, usually found on the dark web, have built-in reputation systems where sellers earn ratings based on the accuracy and freshness of their offerings. This incentivizes higher quality data and weeds out scammers who try to pass off stale or fake credentials.
Interestingly, buyers themselves sometimes provide feedback, highlighting whether credentials were effective in gaining unauthorized access. This dynamic mirrors legitimate online commerce, reinforcing the idea that even in the digital underworld, trust and reputation are key to ongoing business. Honor amongst thieves and all that.
Pricing power and scarcity: What makes credentials valuable?
Not all credentials are created equal. Like any black market, the price of credentials is driven by demand, scarcity, and risk. For instance, login credentials for corporate VPNs, cloud platforms, or financial services accounts can command a premium, especially if they grant access to sensitive data or critical systems.
Factors like two-factor authentication (2FA) can also impact price. Similarly, credentials harvested through weak WiFi security—like those from hotel or café networks—can fetch a decent price on the black market. These are often easier to obtain and may include access to corporate emails or VPNs
In some cases, the geographical location of the credentials matters too. Access to accounts in certain countries or industries—like healthcare or finance—may be more valuable due to local regulatory pressures or the higher blackmail potential. Sellers often bundle these credentials and market them to buyers who specialize in targeting those industries, leaving dark web monitoring tools as the only and last line of defense. .
The buyers’ club: Who’s shopping and why?
It’s easy to assume that every buyer in this black market is a hoodie-wearing hacker in a basement. In reality, the buyers are as diverse as any legitimate customer base. They include low-level script kiddies looking for an easy payday, organized cybercrime groups with sophisticated infrastructure, and even nation-state actors seeking to fuel espionage campaigns.
Some buyers use credentials for direct financial gain—think draining bank accounts or using e-commerce logins to order goods on stolen cards. Others might leverage credentials for lateral attacks, pivoting within a compromised network to steal more data or deploy ransomware. There’s also a growing market for credentials that aid in social engineering, enabling attackers to impersonate real users and carry out targeted phishing or business email compromise (BEC) scams.
Interestingly, some buyers treat credentials as disposable assets, burning through them quickly for one-time scams. Others maintain large portfolios of stolen credentials, using them as strategic tools for long-term operations. This buyer diversity fuels the market’s resilience, ensuring that even as some buyers are caught or exit the game, new ones always arrive to keep demand strong.
Conclusion
The credentials black market is more than just a collection of stolen passwords—it’s a dynamic, evolving hierarchy that mirrors legitimate supply chains in both sophistication and structure. From low-level phishers to elite brokers and diverse buyers, every layer plays a crucial role in fueling the global cybercrime machine.
As technology evolves and cyber defenses improve, so too does the black market’s ingenuity, constantly finding new ways to profit from stolen identities. Staying ahead of this underground economy means understanding how it operates—and keeping your own credentials far from its grasp.